In this book, I will yell the alternate choices at your disposal for encrypting recordsdata the exhaust of open-source machine on a Linux, Mac, or Dwelling windows computer. You would then transport this digital recordsdata across distance and time, to your self or others.
The program “GNU Privacy Guard” (GPG) an open-source model of PGP (Somewhat Ultimate Privacy), permits:
- Encryption the exhaust of a password.
- Secret messaging the exhaust of public/private key cryptography
- Message/Info authentication (the exhaust of digital signatures and verification)
- Personal key authentication (feeble in Bitcoin)
Possibility One
Possibility one is what I’ll be demonstrating below. You would encrypt a file the exhaust of any password you admire. Any particular person with the password can then release (decrypt) the file to scrutinize it. The topic is, how lift out you send the password to somebody in a proper approach? We’re abet to the celebrated topic.
Possibility Two
Possibility two solves this predicament (how-to here). As a replace of locking the file with a password, we can lock it with somebody’s public key — that “somebody” is the supposed recipient of the message. The final public key comes from a corresponding private key, and the non-public key (which only the “somebody” has) is feeble to release (decrypt) the message. With this approach, no silent (unencrypted) recordsdata is ever sent. Very nice!
The final public secret’s one thing that will additionally be disbursed over the accumulate safely. Mine is here, for instance. They’re on the overall sent to keyservers. Keyservers are admire nodes that store public keys. They purchase and synchronize copies of peoples’ public keys. Right here’s one:
You would enter my electronic mail and accumulate my public key in the result. I’ve also stored it here and that you may perchance perchance additionally examine what you chanced on on the server.
Possibility Three
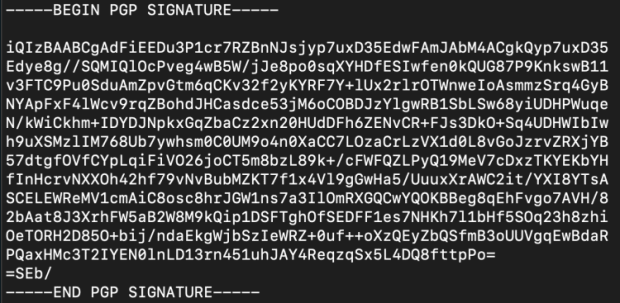
Possibility three is no longer about secret messages. It’s miles about checking that a message has no longer been altered all the map through its birth. It genuinely works by having somebody with a private key stamp some digital records. The records on the overall is a letter or even machine. The approach of signing creates a digital signature (a natty number derived from the non-public key and the records that’s getting signed). Right here’s what a digital signature looks admire:
It’s a text file that begins with a “originate up” stamp, and ends with an “quit” stamp. In between is a bunch of text that genuinely encodes a tall number. This number is derived from the non-public key (a extensive number) and the records (which is de facto continually a number also; all records is zeros and ones to a computer).
Anybody can test that the records has no longer been modified consequently of the celebrated creator signed it by taking the:
- Public key
- Info
- Signature
The output to the seek recordsdata from will be TRUE or FALSE. TRUE potential that the file you downloaded (or message) has no longer been modified consequently of the developer signed it. Very frigid! FALSE potential that the records has modified or the spoiled signature is being applied.
Possibility Four
Possibility four is admire option three, excluding that in want to checking if the records has no longer been modified, then TRUE will point out that the signature used to be produced by the non-public key linked to the public key supplied. In other words, the particular person that signed has the non-public key to the public key that now we salvage.
Apparently, here’s all that Craig Wright would should always lift out to yell he is Satoshi Nakamoto. He doesn’t should always genuinely exhaust any cash.
We already salvage the addresses (identical to public keys) which is probably going to be owned by Satoshi. Craig can then originate a signature along with his private key to those addresses, mixed with any message corresponding to “I genuinely am Satoshi, haha!” and we can then mix the message, the signature, and the take care of, and salvage a TRUE result if he is Satoshi, and a CRAIG_WRIGHT_IS_A_LIAR_AND_A_FRAUD result if he isn’t.
Possibility Three And Four — The Disagreement.
It’s genuinely a matter of what you have faith. Can salvage to you have faith that the sender owns the non-public key to the public key you’ve got, then verification tests that the message has no longer modified.
Can salvage to you don’t have faith the non-public key / public key relationship, then verification is no longer about the message altering, nonetheless the major relationship.
It’s one or the replace for a FALSE result.
Can salvage to you salvage a TRUE result, then you know that BOTH the major relationship is legitimate, AND the message is unaltered consequently of the signature used to be produced.
Glean GPG For Your Computer
GPG already comes with Linux working systems. Can salvage to you are uncomfortable adequate to be the exhaust of a Mac, or God forbid a Dwelling windows computer, then you’ll should always download machine with GPG. Instructions to download and systems on how to exhaust it on those working systems may perchance well additionally just additionally be chanced on here.
You don’t should always exhaust any of the graphical parts of the machine, every thing may perchance well additionally just additionally be done from the teach line.
Encrypting Info With A Password
Invent the secret file. This on the overall is a easy text file, or a zip file containing many recordsdata, or an archive file (tar). Searching on how silent the records is, you may perchance well purchase in mind growing the file on an air-gapped computer. Both a desktop computer built without a WiFi parts, and never to be connected to the accumulate by cable, or that you may perchance perchance additionally manufacture a Raspberry Pi Zero v1.3 very cheaply, with instructions here.
Using a terminal (Linux/Mac) or CMD.exe (Dwelling windows), alternate your working itemizing to wherever you set the file. If that is no longer life like, search the accumulate and in five minutes that you may perchance perchance additionally be taught the answer to navigate the file system specific to your working system (search: “YouTube navigating file system teach suggested” and embody your working system’s title).
From the absolute best itemizing, that you may perchance perchance additionally encrypt the file (“file.txt” for instance) admire this:
gpg -c file.txt
That’s “gpg”, a characteristic, “-c”, a characteristic, after which the title of the file.
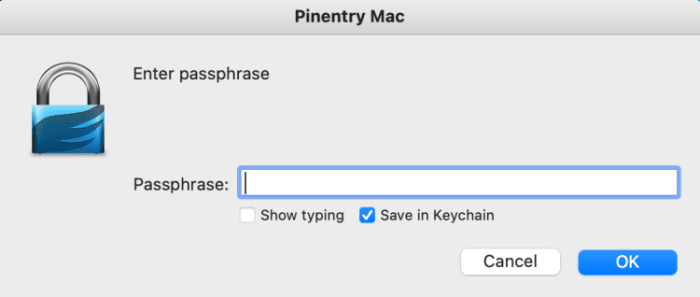
You’ll then be brought about for a password. This can encrypt the contemporary file. Can salvage to you’re the exhaust of GPG Suite on the Mac, test the “Attach in Keychain” is checked by default (gawk below). Which that you may perchance mustn’t set this password if it’s in particular silent.
Whichever OS you utilize, the password will be saved for 10 minutes to the memory. You would definite it admire this:
gpg-join-agent reloadagent /bye
Once your file is encrypted, the celebrated file will stay (unencrypted), and a contemporary file will be created. It’s miles fundamental to solution to a resolution if you will delete the celebrated or no longer. The contemporary file’s title would be the identical because the celebrated nonetheless there’ll be a “.gpg” at the tip. As an instance, “file.txt” will originate a contemporary file called “file.txt.gpg”. You would then rename the file if you desire, or you will salvage named the file by together with extra alternate choices in the teach above, admire this:
gpg -c –output MySecretFile.txt file.txt
Right here, now we salvage “gpg”, a characteristic, “-c”, a characteristic, “–output”, a characteristic, the filename that you may perchance like, a characteristic, the title of the file you are encrypting.
It’s a appropriate advice to put together decrypting the file. Right here is one approach:
gpg file.txt.gpg
Right here is appropriate “gpg”, a characteristic, and the title of the encrypted file. You don’t should always put any alternate choices.
The GPG program will wager what you point out and should always smooth attempt to decrypt the file. Can salvage to you lift out this at this time after encrypting the file, that you may perchance perchance additionally just no longer be brought about for a password consequently of the password is smooth in the computer’s memory (for 10 minutes). In any other case, you’ll should always enter the password (GPG calls it a passphrase).
You’re going to consult with the “ls” teach (Mac/Linux) or “dir” teach (Dwelling windows), that a contemporary file has been created to your working itemizing, without the “.gpg” extension. You would read it from the teach suggested with (Mac/Linux):
cat file.txt
One other solution to decrypt the file is with this teach:
gpg -d file.txt.gpg
Right here is the identical as sooner than nonetheless with a “-d” option as effectively. In this case, a contemporary file is no longer created, nonetheless the contents of the file are printed to the show masks masks.
Which that you may perchance additionally decrypt the file and specify the output file’s title admire this:
gpg -d –output file.txt file.txt.gpg
Right here now we salvage “gpg”, a characteristic, “-d” which is no longer strictly required, a characteristic, “–output”, a characteristic, the title of the contemporary file we desire, a characteristic, and by hook or by crook the title of the file we’re decrypting.
Sending The Encrypted File
You would now reproduction this file to a USB pressure, or electronic mail it. It’s miles encrypted. Nobody can read it as lengthy because the password is appropriate (lengthy and refined adequate) and can’t be cracked.
Which that you may perchance send this message to your self distant places by storing it in electronic mail or the cloud.
Some silly other folks salvage stored their Bitcoin private keys to the cloud in an unencrypted verbalize, which is ridiculously unhealthy. But when the file containing Bitcoin private keys is encrypted with a proper password, it’s safer. Right here is mainly just if it’s no longer called “Bitcoin_Private_Keys.txt.gpg” – Don’t lift out that!
WARNING: It’s most fundamental to design end that in no approach am I encouraging you to position your Bitcoin private key recordsdata on a computer (hardware wallets were created to point out that you may perchance perchance additionally never should always lift out this). What I am explaining here is for particular cases, below my steerage. My students in the mentorship program will know what they are doing and should always smooth only exhaust an air-gapped computer, and know the overall capacity dangers and concerns, and ways to steer definite of them. Please don’t form seed phrases correct into a computer until you are a security knowledgeable and know precisely what you are doing, and don’t blame me in case your bitcoin is stolen!
The encrypted file may perchance also be sent to one more particular person, and the password may perchance well additionally just additionally be sent separately, perchance with a various communication machine. Right here is the less advanced, and no longer more proper approach, compared with option two explained at the starting of this book.
There are genuinely all kinds of ways in which you may perchance perchance additionally invent the birth of a secret message across distance and time. Can salvage to you know these instruments, think arduous and carefully about the overall dangers and eventualities, a appropriate opinion may perchance well additionally just additionally be made. Or, I am in the market to assist.
Ultimate ideal fortune, and gay Bitcoining!
Right here’s a customer post by Arman The Parman. Opinions expressed are completely their possess and lift out no longer necessarily mirror those of BTC Inc or Bitcoin Journal.