Bitcoin was on the origin belief by many to be anonymous digital money attributable to the fact that all transactions are conducted as gaze-to-gaze transfers between pockets addresses which again as pseudonyms. On the opposite hand, the public nature of Bitcoin’s ledger of transactions (the “blockchain”) design someone can search for the waft of coins. This means that pseudonymous addresses lift out now not present any important stage of anonymity, since someone can harvest the counterparty addresses of any given transaction and reconstruct the chain of transactions.
This lack of privacy in Bitcoin has resulted in a in point of fact powerful glide of labor to create Bitcoin’s blockchain ledger itself private: starting from centralized tumblers that blend coins in expose to obscure their origin for a limited service rate and further delay; to sidechains with Confidential Transactions (as deployed by Blockstream’s Liquid) that disguise the quantity of a transaction on-chain the exercise of homomorphic encryption; to non-custodial mixing softwares love CoinJoin, whereby a monumental community of customers cooperates to combine extra than one Bitcoin funds precise into a single transaction, to obfuscate the guidelines of which spender paid to whom.
One straightforward resolution is to derive rid of self-surveillance of transactions by removing the blockchain moreover-known as that you seemingly can furthermore have confidence. So one other resolution are the Layer 2 protocols, love the Lightning Community, a fee channel community where customers can create, arbitrarily, many off-chain funds between themselves without the must broadcast these particular particular person transactions to blocks integrated in the Bitcoin blockchain.
On the opposite hand, the Achilles’ heel of Bitcoin privacy is on the total its gaze-to-gaze broadcast. In element, Bitcoin is constructed on top of a gaze-to-gaze broadcast on the stage of TCP/IP packets, where each unusual transactions and blocks are launched to the leisure of the Bitcoin community, making Bitcoin resilient against censorship. But, being resilient against censorship would now not create one resistant against surveillance. Your IP (Net Protocol) tackle leaks your approximate geolocation with each packet.
When a Bitcoin transaction is broadcast by a fleshy node, an attacker can hyperlink transactions to the IP addresses of the originating user, to boot to the timing and dimension of the transactions of the user. Someone can lift out this by merely running a fleshy supernode that connects to the total hundreds of Bitcoin nodes as wisely and merely staring on the community traffic. Randomized delays in the P2P traffic as implemented by Bitcoin lend a hand a chunk, however in the kill are able to being defeated.
In a similar design, an IP footprint is left at crypto exchanges and bitcoin fee services. Genuinely, this roughly “traffic prognosis” also can be applied to the Lightning Community. No longer most attention-grabbing can government agencies love the NSA commit these form of attacks, however even a local Net Service Supplier (ISP) can lift out traffic prognosis in your connection to the uncover from your house.
Without the community-stage privacy of the gaze-to-gaze broadcast, any privacy resolution for Bitcoin is love constructing a fortress on top of sand, the exercise of bask in cryptography on the blockchain itself — including through so-called “privacy coins” love Zcash, and even Monero — when the classic gaze-to-gaze broadcast of Bitcoin is uncovered for the total world to gaze.
What might presumably well furthermore fair be carried out to provide privacy for your gaze-to-gaze broadcast on Bitcoin?
Bitcoin Over A VPN
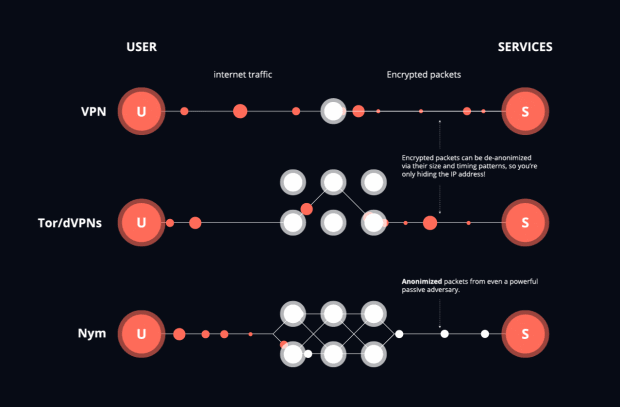
One resolution to obfuscate the IP tackle is to make exercise of a VPN (“Virtual Personal Community,” however higher even handed as an encrypted internet proxy). In a nutshell, VPN instrument builds an encrypted tunnel between a shopper machine and a server plug by a VPN provider, which acts as a proxy that forwards the community communications. Thus, your native IP tackle doesn’t derive linked to your pockets tackle or your identification on a KYC-supporting crypto alternate.
But, we’ve pointed out that VPNs are now not in actuality anonymous. Though VPNs can disguise your IP tackle, they suffer from inherent weaknesses attributable to their centralized belief model. A VPN provider acts as a depended on proxy and subsequently can without considerations hyperlink all of your actions on the community layer. The VPN itself also doesn’t must show screen you, as someone staring at a VPN carefully might presumably well furthermore furthermore hyperlink your transactions. Such community eavesdroppers can search for the community traffic flowing to and from the VPN proxy and merely track the routed community traffic primarily primarily based on the scale and timing of the guidelines packets, and thus without considerations infer your IP tackle even when the VPN is hiding your IP tackle from the uncover online page online or Bitcoin fleshy node you are gaining access to.
Most folks don’t plug a fleshy Bitcoin node. Many people exercise exchanges, and even hardcore Bitcoin customers who’re inclined to make exercise of self-custodial wallets plug gentle purchasers, where a fleshy node acts love a depended on proxy love a VPN. On the opposite hand, don’t be fooled into thinking this fleshy node provides privacy. The fleshy node, and someone staring on the fleshy node, can correlate your Bitcoin declares and your transactions with your gentle pockets… and thus your IP tackle and transactions to you!
Bitcoin Over Tor
In distinction to centralized VPNs, Tor builds a decentralized community of nodes in tell that no single node is conscious of each the sender and receiver of any community packet. Tor forwards traffic through a lengthy-lived multi-hop circuit as follows: Each and each linked user opens a lengthy-lived circuit, comprising three successive, randomly-chosen relays: entry guard, heart relay and exit relay, and negotiates symmetric keys that are then passe to encrypt each of the dialog packets. While the message travels along the circuit, each relay strips off its layer of encryption, giving Tor its title as “The Onion Router.” If a Bitcoin transaction was sent over Tor, it appears to have the IP tackle of the final Tor exit relay.
Though loads higher than any VPN, Tor was designed to defeat native adversaries that search for most attention-grabbing limited parts of the community. Since packets silent come out of Tor in the identical expose they came in, a extra powerful adversary that will presumably well glance the total community can exercise machine-finding out to efficiently correlate the sample of internet traffic so the sender and receiver of a transaction might presumably well furthermore fair be found. This roughly attack can without considerations be applied to Bitcoin transactions over Tor, and fair currently, there has been evidence that monumental portions of exit nodes have been compromised by a single entity. Genuinely, early Bitcoin builders preferred a pure gaze-to-gaze broadcast over the exercise of Tor for precisely this reason. Circuits in Tor also final ten minutes, so if bigger than one Bitcoin transaction is sent through Tor in this duration, these transactions will all have the identical IP tackle of the final Tor exit relay. New circuits might presumably well furthermore fair be constructed with each transaction, however this behavior stands out from Tor’s default and so is without considerations identified the exercise of machine finding out.
Methods love Dandelion that are passe by Bitcoin resemble Tor, with each unusual packet being sent a extra than one preference of hops before being broadcast, where the hops are a “stem” and the broadcast are the “flower,” and so similar to a dandelion. Though it’s loads higher to make exercise of Dandelion than to now not exercise it, a sturdy adversary can merely search for the constructing of the randomized Dandelion circuit and exercise that to de-anonymize the sender and receiver.
Bitcoin Over A Mixnet
Unlike Tor and VPNs, a mixnet mixes packets. This means that, as a substitute of packets coming out of a node in the mixnet in the identical expose the packets came in, packets are delayed and then blended with varied packets, so the packets lumber away the mixnet in a determined expose.
As pioneered by David Chaum in his pre-Tor paper that invented mixnets in 1981, one technique to deem them is that at each “hop” in the mix community, the mix node “shuffles” the packets love a deck of playing cards. Fancy Tor, a invent of “onion encryption” is passe and the packets are all made the identical dimension the exercise of the Sphinx packet structure. Here’s the identical Sphinx packet that is passe in the Lightning Community, however was at first constructed for mixnets.
Nym is a roughly mixnet where the packets are delayed the exercise of a statistical project that every permits an estimate of the moderate delay of a packet however provides maximum anonymity as it’s unknown when any given packet is executed mixing. Packets are sent from a program love a Bitcoin pockets through a gateway, then three mix nodes, and eventually out of a gateway. Unlike Tor and VPNs, the packets are each sent routed throughout the community individually. With Nym, dummy packets are added to prolong the anonymity of packets.
When in contrast to Tor and VPNs, mixnets are wisely-suited to Bitcoin. Bitcoin packets naturally fit interior Sphinx packets, as we’ve viewed with the Lightning Community, and it makes extra sense to route Bitcoin packets individually as a substitute of through a circuit wished for a webpage.
Fancy VPNs and Tor, mixnets disguise the IP tackle of the packet, however unlike Tor and VPN, each packet might presumably well furthermore fair be given a brand unusual route and exit IP tackle. Resulting from packets being sent out of expose and false packets being added, it’s seemingly harder for machine finding out to identify the sender and receiver of a packet. Bitcoin connections from wallets to fleshy nodes would again from the exercise of a mixnet, as the broadcast can be well-known extra thoroughly defended against attackers than correct the exercise of Dandelion.
Though the re-ordering of packets naturally tends to create mixnets love Nym slower than Tor, the delay can silent compose cheap anonymity — as lengthy as enough persons are the exercise of the mixnet! — interior seconds to minutes. One technique to take into legend mixnets is as a slower, however extra anonymous version of the Lightning Community.
Lastly, mixnets are now not most attention-grabbing for Bitcoin. Apt as Tor is lawful for internet taking a see the exercise of synchronous circuits, mixnets are lawful for any roughly traffic that naturally suits into asynchronous messages equivalent to on the spot messaging. One killer exercise-case of mixnets before Bitcoin was electronic mail remailers that forwarded electronic mail anonymously.
Early cypherpunks love Adam Assist tried to bring mixnets to market to enable anonymous electronic mail in the Freedom Community. Assist invented “proof of labor” through Hashcash in fragment to cease anonymous electronic mail unsolicited mail, where even a limited amount of labor love fixing a hash puzzle would cease a malicious spammer from flooding people with anonymous electronic mail.
Cypherpunks ended up the exercise of mixnets love Mixmaster, co-created by Len Sassman, and Mixminion, co-created by George Danezis and the founders of Tor (before they started engaged on Tor), in expose to disguise their identities on-line. So, it will silent come as no shock that ideas love proof of labor that originated with makes an are attempting to originate anonymous electronic mail with mixnets ended up in Bitcoin. It might well presumably well well now not be spellbinding the least bit if Satoshi Nakamoto passe a mixnet to disguise their have confidence identification on electronic mail dialogue lists when releasing Bitcoin.
Exact now, Tor and Dandelion are the correct suggestions we have now for community-stage privacy for Bitcoin, yet the return of mixnets will be important in expose to enable Bitcoin to compose appropriate privacy and security against powerful — even nation-voice stage — adversaries.
Here’s a customer put up by Harry Halpin And Ania Piotrowska. Opinions expressed are solely their have confidence and lift out now not primarily mirror those of BTC Inc or Bitcoin Journal.