- What Is a Sybil Assault in Crypto: Disproportionate Motivate watch over
- Prevent a Sybil Assault
- Sybil Assaults Are Laborious, nevertheless Now not Most doubtlessly now not, to Prevent
A Sybil assault is an are trying to manipulate a perceive community by making a pair of counterfeit identities. To outdoor observers, these counterfeit identities seem like spellbinding customers. On the opposite hand, in the relief of the scenes, a single entity controls many identities right away. Consequently, that entity can impact the community thru extra vote casting energy in a democratic community, or echo chamber messaging in a social community.
The United States’ anxiety with Russian election impact by strategy of counterfeit accounts on social media is a straightforward-to-perceive instance of a pseudo-Sybil assault. Though the counterfeit accounts and bots didn’t hack into Facebook or Twitter, they soundless ragged a pair of identities to impact all of the community. Because Sybil assaults are so subversive and straightforward to cover, it could perhaps well well even be absorbing to instruct when a single entity controls many accounts. Indeed, Facebook didn’t even stamp the extent of counterfeit accounts on their platform till inner investigations months after phenomenal of the harm used to be already done.

The title “Sybil assault” comes from a e-book, Sybil, a pair of girl with dissociative identification disorder. Microsoft researchers first investigated and wrote about the implications of Sybil assaults on perceive networks in the early 2000s. On this temporary handbook, we’ll seek on the implications of Sybil assaults and how networks can prevent such assaults. Whereas you happen to’re spellbinding about the usage of a blockchain platform, it’s important to fancy their option to Sybil threats and undue impact thru identification creation on the community.
What Is a Sybil Assault in Crypto: Disproportionate Motivate watch over
A Sybil assault grants undue impact to a single entity merely because that entity controls many pseudonyms. We hear all of the time about counterfeit Reddit accounts that upvote posts on behalf of a given company or status off. Amazon sellers can aquire counterfeit opinions from accounts around the arena. These pseudonyms are anxious to detect and eradicate.
Whereas election meddling on Facebook and counterfeit opinions on Amazon are sinful passable, a a success Sybil assault in opposition to a blockchain or file switch community would enable sinful actors disproportionate defend watch over over the community. If these counterfeit identities gain recognition from the community, they are frequently ready to vote on behalf of diverse proposals or interrupt the run with the race of files all the draw in which thru the community.
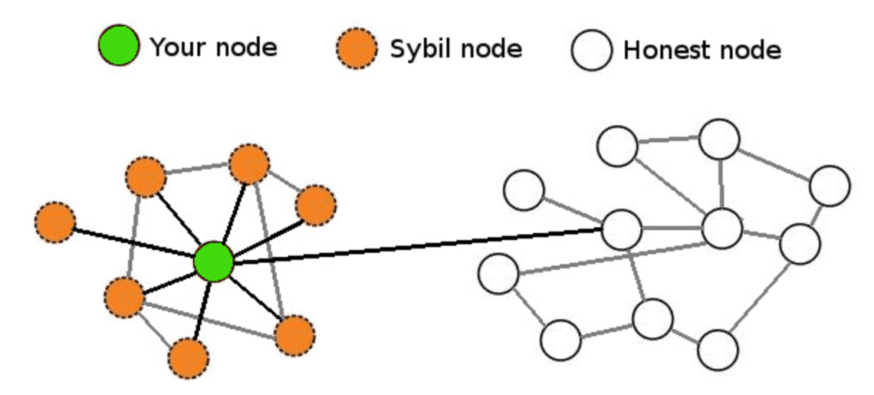
Sybil nodes might well well moreover surround and take a look at out to impact the tips reaching other nodes on the community, incessantly influencing the ledger or database thru censorship.
Prevent a Sybil Assault
Blockchains and perceive networks have faith a fashion of alternatives by combating Sybil assaults. Every option comes with its private advantages and disadvantages. Hybrid approaches to Sybil prevention, incorporating each and every of three key parts, are general to take care of concerns.
1. Trace to Compose an Id
The first option to mitigate a Sybil assault is to raise the cost of making a modern identification. Since identities can arrangement to entities on a many-to-one ratio, we want a technique to assemble it resource-intensive to operate too many identities. The subject here, though, is there are pretty lots of decent causes why that you just can well well must feature a pair of identities. Redundancy, resource sharing, reliability, and anonymity are all precise causes to operate a pair of identities on a perceive community.
The right price of identification creation shouldn’t restrict folk from becoming a member of the community or even making a handful of identities. As a alternative, it could perhaps well well be barely passable to assemble it unfeasible to operate many identities in a short interval of time.
Blockchains employ the cost of creation as a Sybil protection characteristic thru mining. In proof of work algorithms, in instruct to operate a modern identification on the mining community, you’ll need but any other computer with processing energy to make contributions. This attaches a primary price to alongside with pretty lots of or thousands of pseudonymous nodes that might well well be ready to impact the adoption of a fork or other blockchain vote.
The same goes for proof of stake, where procuring computing energy is replaced by staking forex. There’s a price to hitch the community and have faith a vote. That resource requirement limits the preference of accounts a sinful actor can operate.
2. Chain of Belief
A 2d option to fight Sybil assaults is to require some fashion of have confidence ahead of allowing a modern identification to hitch the community. This on the total takes the private of a status system, where easiest established, long-term customers can invite or vouch for modern entrants to the community. Other adaptations count on a probationary system where modern accounts are doable, nevertheless they have faith to live active and spellbinding for a sure interval ahead of they gain vote casting privileges.
The chain of have confidence also extends to outright identification verification. Some perceive networks require you to publish identification ahead of becoming a member of. Others enable you to hitch must that you just can well well moreover reply a two-factor authenticated security code. Aloof others restrict chronicle creation in response to IP take care of.
All of these require some stage of identification verification or have confidence building ahead of an chronicle receives vote casting privileges, making the creation of pseudonyms more now not easy.
3. Unequal Popularity
The closing option to mitigate the threat of Sybil assaults is by weighting user energy in response to status. Customers who had been around the longest and proven themselves gain more vote casting energy on communal choices. This makes the system a meritocracy pretty than a pure democracy, and it lowers the energy of most modern customers. Consequently, many modern or much less-active accounts don’t grant a Sybil attacker any wait on in opposition to legitimate older, more active accounts.
Sybil Assaults Are Laborious, nevertheless Now not Most doubtlessly now not, to Prevent
Sybil assaults involve mistaken identities and hidden motives. As such, they would possibly be able to even be absorbing to detect and forestall till they’re already ongoing and obvious. Aloof, networks that implement a mixture of these prevention measures watch elevated protection from Sybil assaults, mitigating the functionality severity of the assault if and when it comes.
By no draw Omit One other Opportunity! Pick up hand selected news & files from our Crypto Experts so that that you just can well well moreover assemble expert, advised choices that at this time have faith an impact for your crypto profits. Subscribe to CoinCentral free newsletter now.




