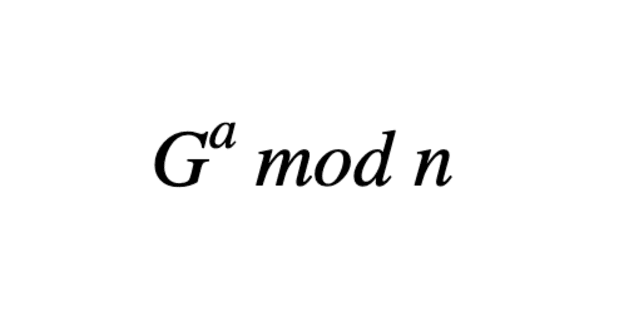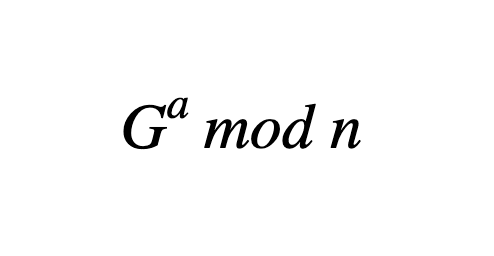I’m going to talk in regards to the security within the abet of Bitcoin addresses and keys, called Public Key Cryptography. This entails SHA256, Random Quantity Mills(RNGs), Hash Functions, and Elliptic Curve Digital Signatures (ECDSA.) If you happen to’ve questions previous this, please in actuality feel free to DM me. I am a mathematician by practicing, and I in actuality have a deep cherish for it. If you happen to get hold of that you have got a recent hobby in cryptography as a ardour, there are many people that form cryptographic algorithms for stress-free, and their neighborhood could possibly even be truly helpful to your chase.
I promise that you greatest need some current algebra for this, as successfully as a straightforward figuring out of exponential functions. If you happen to could possibly well presumably be conversant in modular arithmetic, that’s unbelievable. If now not,no biggie.
Cryptography has been around for thousands of years, and currently has a extremely sturdy neighborhood of pros and hobbyists alike. The expertise has advance an extremely famous distance, and its present iterations enable for the procure security which we rarely prefer to mediate of.
Let’s delivery with the belief of Public Key Cryptography, particularly at some stage within the context of Bitcoin. On the commonest level, PKC entails your interior most keys, and the public keys generated from them. PKC utilizes what are called “trapdoor functions” which would be easy to resolve (easy to generate a public key from a non-public key), but nearly not most likely to reverse engineer (get hold of a non-public key given a public key.) Here’s attributable to the usage of modular arithmetic, exponential functions, and in actuality clear top numbers.
Your bitcoin interior most keys are doubtlessly phrases, but they’ll moreover be a extremely clear number. To be reveal, when we delivery the encryption, your interior most keys shall be converted to a clear number or binary string (sequence of ones and zeros) irrespective of what its initial execute used to be. How clear! Here’s why people every so often command your interior most keys “describe a extremely, very clear number” and is the goal of its security. Whereas right here’s technically proper in a deterministic/algorithmic sense, it’s now not necessarily obvious why.
Deepest key generation is one other spirited aspect. Hardware and custodial wallets comprise this for you, and so they could possibly well or could possibly well now not account for you precisely how they slither about it (inaugurate-source vs closed-source tool.) Here’s positively price brooding about when picking a pockets. The diversified possibility is to form your have from scratch. You could possibly well roll a good die, flip a coin or employ some diversified a similar methodology. There are moreover online random number generators which had been tested and graded by the expert cryptography neighborhood. RNGs steadily employ the present time as their generator to form a minute initial distinction which, after ample iterations, makes a fully extraordinary number. Settle a web RNG at your have risk. Even though the RNG itself is comely, there would be malware on the positioning. The extra you appreciate!
So we have now our secret phrases. Let’s look what occurs subsequent.
Here’s a rather easy execute of our trapdoor feature. “G to the a mod n” represents our final public key (mod is short for modular arithmetic, which restricts our system to a favorable restrict of numbers, versus every single pure number). But, even when you appreciate G and n, there’s no easy procedure so that you can get hold of a, which represents your interior most key. Calculating G to the mod n in all equity easy, but there’s no going backwards, attributable to the Discrete Log Direct. N is fundamentally a clear top number attributable to they’re unfactorable by definition. Also, If relative complexities of functions/concerns hobby you, in actuality feel free to look into Algorithm Time Complexity.
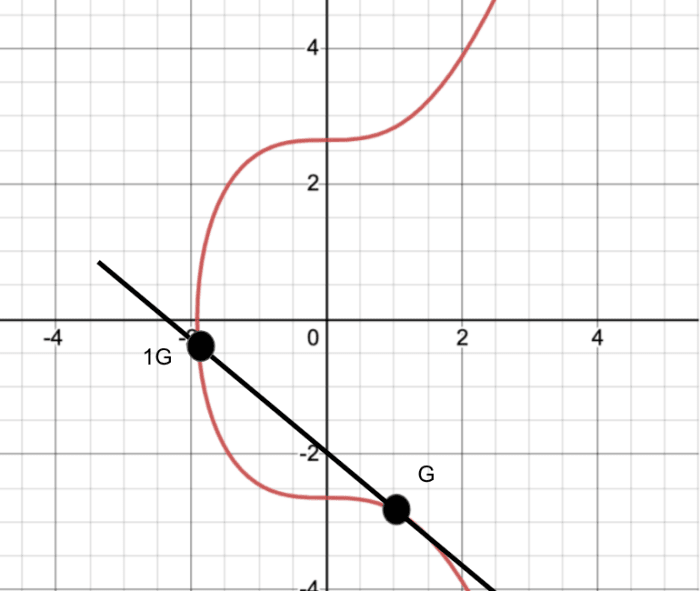
Let’s slither a bit deeper, and test it graphically for a extra concrete figuring out.
The crimson line is our curve, and is the reveal one former by Bitcoin’s ECDSA. G is the point we delivery at, our “generator,” when you’re going to. Then, we are going to “add” G to itself (even if it isn’t addition within the same old sense – these loopy mathematicians fancy to redefine things. Don’t even get hold of me started on topology!). On this case, alongside side it procedure we are going to employ the tangent line of this point. Wherever that tangent line intersects the curve shall be our subsequent point. We can yet again employ the tangent, and get hold of a recent point. In be conscious (on a computer) right here’s being performed many thousands, or even thousands and thousands, of times. The stop consequence is that even when you appreciate the establish I started, you don’t know how yet again and yet again I “added” G to itself in describe to get hold of to the final point. How yet again and yet again we performed the addition is your interior most key (your interior most number). Again, right here’s easy to establish given a most likely solution, but nearly not most likely to “brute force.” Voila!
So we have now our first deterministic (one enter offers you one solution) scrambling of files, on the choice hand it’s now not in a huge layout (ethical now, it’s ethical an ordered pair (x,y). We have a public key, derived from a non-public one. Let’s fade that files yet again and transform it.
We comprise this by the employ of SHA 256, which stands for Salvage Hashing Algorithm. A Hashing Algorithm is a reveal location of steps one applies to files, which leads to an encrypted dataset of mounted dimension, irrespective of the scale of the enter.
Optimistic, this family of algorithms used to be developed by the United States National Security Company (NSA), but don’t let that concern you. The wonder of utilized science — alongside side arithmetic, is that discovery and files stand fair of who developed it. Here’s why we have now proofs. If a proof is “sound,” then it stands by itself two toes, and could possibly well now not be “hacked” or labored around. The SHA2 family is public files. You could possibly well slither surfing and test the code, and when you fancy employ SHA256 your self to encrypt some things. You’ll get hold of that a extremely minute exchange in enter can have a dramatic output on the answer. Chaos Belief is ravishing. But anyways.
As many people stable billions of bucks with SHA256, they’ve moreover spent plenty of money attempting out it to create sure its security. Folk steadily bring up quantum computing as a most likely procedure to interrupt this encryption. Alternatively, were quantum computing to alter into feasible, there is a ways extra cash to be stolen by hacking the cease 5 most main banks on the earth. I’m sure Bitcoin is a ways down the checklist since, as soon because it used to be hacked, its price would doubtlessly decrease dramatically. All that being mentioned, if SHA256 becomes much less stable at some point, we can repeatedly upgrade Bitcoin’s encryption strategies. Programmable money!
SHA256 is such as ECDSA in that it’s easy to establish an solution, but very complicated to brute force — attempting every solution till you get hold of the ethical one. SHA256 is so named attributable to it creates a string of 256 bits — a chain of 256 zeros and ones. This makes for an absurdly excessive number of most likely combos, bigger than the number of atoms within the observable universe.
We’re going to employ a diversified hash yet again in describe to get hold of a smaller output, which makes for a shorter final take care of. This hash feature is called RIPEMD-160. After we have now this consequence, we are going to convert it into what’s called Unhealthy58, which is ethical a execute that’s extra readable for humans.It omits both the number zero (0) and the uppercase letter O (o), so that they aren’t incorrect for every diversified, as successfully as omitting the uppercase letter I (i), so that it isn’t incorrect for the #1 (1) or the decrease case letter l (L) It omits both the number zero (0) and the uppercase letter O (o), so that they aren’t incorrect for every diversified, as successfully as omitting the uppercase letter I (i), so that it isn’t incorrect for the #1 (1) or the decrease case letter l (L).
And now we have now a public take care of which is provably (in a proper, mathematical sense) constituted of a diversified interior most take care of. Even though all seven billion people on the earth form a recent bitcoin public key day-after-day for a thousand years, there are so great of potentialities that the probability of rising the same one twice is quite zero.
All of right here’s rather the scheme, rising and verifying keys, subsequently our ten minute common block time. Ten minutes for mathematically-assured final settlement is price all the things.