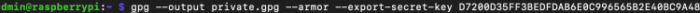As a Bitcoiner, you’re going to want a genuine methodology to order privately, with out relying on a firm to encrypt your recordsdata for you. As an illustration, freely on hand techniques with stop-to-stop encryption cherish Telegram (no longer with its default possibility) and Signal and others are straightforward to make utilize of, but I don’t fully trust them.
This text will demonstrate you techniques to send messages utilizing free originate-source machine, GNU Privateness Guard (gpg), which permits encryption and decryption utilizing public and inner most key cryptography. It’s extra advanced in the starting to DIY, but while you net the hold of it, it’s no longer that onerous. I’ll bewitch you through it grade by grade, genuine be conscious along and bookmark this text for future reference.
Right here’s a petite extra background about gpg (including pgp) for those that must dig deeper. It’s of ardour to illustrate that public and inner most key cryptography isn’t any longer only old for encryption and decryption, but additionally old for the verification of digital signatures — old in Bitcoin transactions and additionally recordsdata in long-established (e.g., checking if the machine you downloaded is loyal and no longer tampered with, as proven in the first video here).
How It Works
To net a public and inner most key pair, your computer generates a extraordinarily huge (“unguessable”) random amount from which the gpg machine will net for us a private key, and from that, a public secret’s created (genuine cherish Bitcoin inner most keys, extra info here).
The general public secret’s shared with the arena (cherish a Bitcoin contend with) and accommodates your ID (electronic mail and title) which you publish on-line. Right here is mine. Think of the public key cherish an originate genuine. Anyone can write a message and encrypt that message along with your PUBLIC key (i.e., establish it to your genuine and lock the door shut) — only you’ve the inner most key and, therefore, only it’s also possible to originate your genuine (i.e., decrypt and read the message).
A aspect demonstrate: Don’t grief about this for now — genuine demonstrate that, in Bitcoin, there might be not one of these thing as a “encryption” going on with payments. As a substitute, there are “signatures” made with inner most keys, which is ready to be “verified” by anybody utilizing public keys.
Overview
In this recordsdata, I’ll bewitch you throughout the following steps:
- Download gpg.
- Construct your admire inner most and public key.
- Retailer your inner most key to a USB power.
- Upload your inner most key to your utterly different computer’s’ keychain.
- Upload your PUBLIC key to a keyserver and/or your online page material.
- Upload your public key’s fingerprint to your on-line profile, e.g., Twitter or Keybase.
- Send me a message encrypted with my public key, and I will answer encrypting along with your public key.
Download GPG
The very first thing you’ll must full is salvage the gpg machine.
Linux
Whenever you’re utilizing Linux, gpg must quiet already be installed. If no longer, it’s also possible to install it with the reveal:
sudo supreme-net install gnupg
Whenever you genuine would prefer to examine if it’s installed, form this:
gpg –version
HINT: Whenever you’re running a Bitcoin Node on a Raspberry Pi, it’s also possible to in point of fact utilize SSH to net precise of entry to your Pi’s terminal and lumber gpg commands cherish that. If what I acknowledged isn’t life like, don’t grief, ignore it, it’s originate air the scope of this text.
Mac
Whenever you’ve a Mac, you’ll must salvage and install “GPG Suite” — it’s free except you additionally settle on the electronic mail tools (no want). This is in a position to perchance well present the reveal line tools you will want.
Home windows
Download and install “Gpg4Win.” It’s free. There is a donation web bid sooner than downloading, it’s also possible to take $0 to proceed.
When inserting in, it’s also possible to uncheck the entire containers excluding the first.
Construct Your Relish Personal and Public Key
Originate the terminal in Mac or Linux or reveal urged in Home windows.
Form:
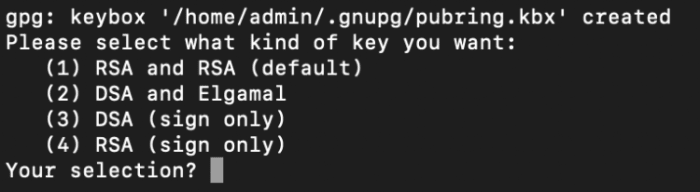
gpg –fleshy-generate-key
Snatch the default RSA possibility.
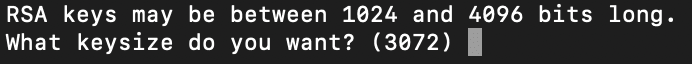
Then spend the size of your key. Larger is extra genuine.
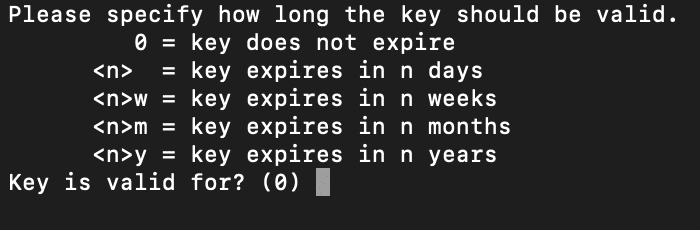
Then take how lengthy the principle must quiet be legitimate. I desire no longer to let the principle expire.
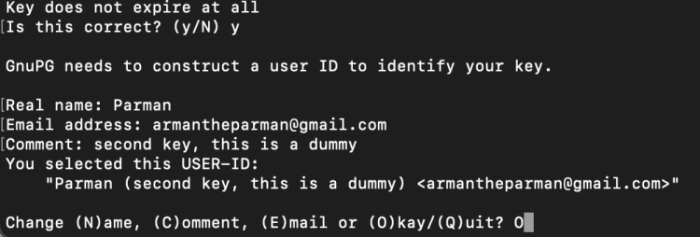
Then you’ll absorb out some private petite print. This can also even be made public so other folks know who the public key belongs to. The tips in point of fact will get embedded into the principle. Snatch “O” for “Okay” to proceed.
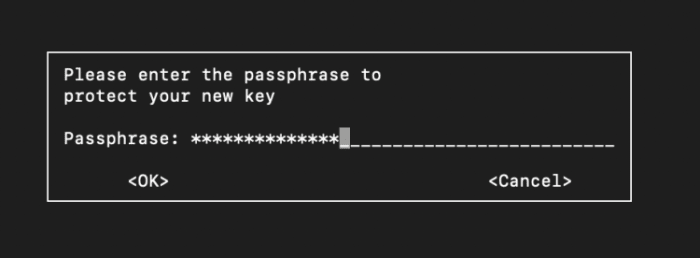
Then lock your inner most key with a “passphrase.”
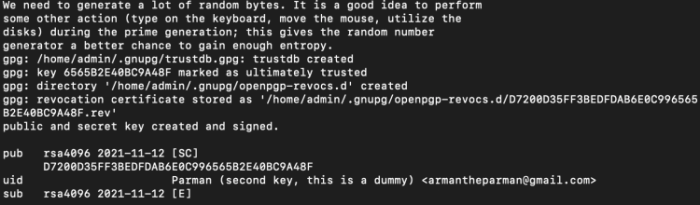
I was as soon as told to switch the mouse around or form on the keyboard during key introduction so to add some extra randomness to the principle. These are the petite print of the principle I created (on the bottom).
Retailer Your Public Key To A USB Power
The computer you old to net the inner most key has the principle in its “keychain,” and it’s locked with a passphrase. The keychain is genuine an abstract thought — the principle(s) are in point of fact genuine saved in a file someplace.
I imply you backup your inner most key to a USB thumb power. This helps you to replica it to a explain computer if wanted and reduces the anguish of loss.
To prevent that, we first must export it from the keychain and establish it precise into a file.
Originate by getting the principle’s ID:
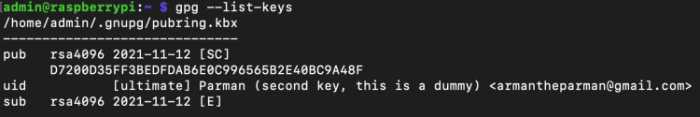
gpg –checklist-keys
This presentations you the entire keys (public and inner most) to your computer’s keychain.
Reproduction the principle ID to the clipboard. Mine is:
D7200D35FF3BEDFDAB6E0C996565B2E40BC9A48F
Then we export the public keys to a file, and now we must establish the principle ID in the reveal (that’s why we copied it to the clipboard).
The above reveal uses gpg and has some alternatives.
The “–output” possibility specifies that the output must quiet scurry to a file, offered straight after.
I chose “public.gpg” because the title of the file, and it might perchance well also be created because the reveal is done.
“–armor” specifies the output must quiet be in ASCII-armored structure and “–export” specifies which key from the keychain must quiet be exported, offered straight after.
Whenever you would prefer take a look at the contents of the file, genuine utilize the “less” reveal (‘q’ exits the ‘less’ feature):
less public.gpg
Subsequent, let’s export the inner most key. The reveal is cherish the one sooner than with some adjustments. Commerce the file title to one thing cherish “inner most.gpg” and substitute the “–export” possibility to “–export-secret-key.”
We now admire got “public.gpg” and “inner most.gpg” files in the current checklist. Reproduction them to a USB power and spend them genuine and hidden. It’s no longer as sensitive as a Bitcoin inner most key, but the loss or theft of the “inner most.gpg” file would allow someone to impersonate you. In case your passphrase is stable, it’s unlikely an attacker will likely be ready to make utilize of your inner most key even in the occasion that they got their grubby palms on it.
Upload Your Keys To Your Other Laptop’s Keychain
Snatch your USB power along with your inner most key to your utterly different computer. Be clear gpg is installed. Originate a terminal and navigate to the establish of residing of your file. Enter the reveal:
gpg –import inner most.gpg
Endure in thoughts “inner most.gpg” is a file title, so replace that along with your file’s title, don’t genuine blindly replica the reveal with out thinking. You are going to be asked to enter the passphrase, and then the inner most and public keys will likely be imported in a single scurry.
To delete the inner most key, the reveal is:
gpg –delete-secret-keys KEY_ID
Change KEY_ID for the principle ID or electronic mail of your key.
Upload Your PUBLIC Key To A Keyserver And/Or Your Net page
There are a complete lot of in model keyservers in utilize around the arena. The main keyservers synchronize themselves genuine cherish Bitcoin nodes stop, so it’s some distance comely to select a keyserver near you on the web and then utilize it customarily for sending and receiving keys (PUBLIC keys, after all).
gpg –keyserver keyserver.ubuntu.com –send-key D7200D35FF3BEDFDAB6E0C996565B2E40BC9A48F
The above reveal is on one line. There is a plan after “–send-key” which might perchance well no longer be evident because the formatting to your browser might perchance well destroy the line into two.
“–keyserver” is an possibility that expects the net contend with of a keyserver subsequent.
“–send-key” is an possibility that expects a Key_ID.
Whenever you would prefer import a public key of someone else straight from a keyserver, enter the above reveal but substitute “–send-key” to “–recv-key,” and utilize his or her Key_ID.
Upload Your Public Key’s Fingerprint To Your Twitter/Keybase
What’s the level of this? Whenever you demonstrate a short version of your public key in varied areas, someone sending you a message can also even be extra clear that they’re downloading the supreme public key.
You can also take a look at your key’s fingerprint with this reveal:
gpg –fingerprint KEY_email
With a amount of these commands, customarily an electronic mail will work, customarily it wants the valid KEY_ID. You can also continuously take a look at what your KEY_ID is with:
gpg –checklist-keys
While you take a look at your fingerprint, replica it and paste it into your on-line profiles as I even admire carried out on Twitter.
Whenever you occur to salvage my public key, the fingerprint will likely be displayed after you import it, or in the occasion you utilize the “–checklist-keys” reveal, or “gpg –fingerprint Key_ID”.
You can also then examine the output with my on-line profile to be clear you’ve the supreme key.
Send Me A Message Encrypted With My Public Key, And I Will Acknowledge Encrypting With Your Public Key
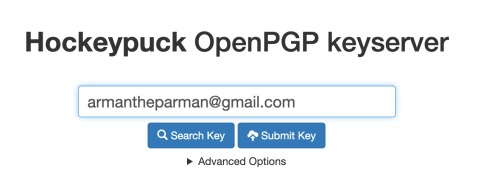
First, you’ll must net my public key. You can also browse to keyserver.ubuntu.com, and enter my electronic mail into the quest field.
Or it’s also possible to scurry to my contacts/gpg web bid and be conscious directions there. Reproduction my Key_ID to the clipboard.
Originate a terminal and enter this reveal:
gpg –keyserver keyserver.ubuntu.com –recv-keys e7c061d4c5e5bc98
You now admire my public key imported to your computer’s keychain.
Now it’s also possible to form a letter to me in a textual bid material file (letter.txt) or Be conscious doc (anything else, no doubt) and fix it to disk. In a terminal, navigate to where you saved the file. Then form this reveal:
gpg –output letter.gpg –encrypt –recipient armantheparman@gmail.com letter.txt
Right here you’ve got a reveal which is ready to be all on one line. The “–output” possibility helps you to net a filename typed straight afterward, where the encrypted recordsdata will scurry.
The “–encrypt” possibility is an instruction to encrypt.
The “–recipient” possibility helps you to spend which public key to your keychain to make utilize of to encrypt the message. Immediately afterward, in the occasion you form in an electronic mail contend with, it might perchance well perchance spend the upright key out of your keychain.
In the end, following the electronic mail or Key_ID, you establish the title of the file you would prefer encrypt.
You can also net some warnings and affirmation messages, but after that, you will want to quiet admire a brand new file called “letter.gpg” or regardless of filename you chose. The long-established file quiet exists (“letter.txt”). You can also delete that file with (utilizing Linux or Mac):
rm letter.txt
You can also additionally clear the history of the reveal urged with:
history -c
You can also then send an electronic mail and establish “letter.gpg” and send it to me. After I receive it, I will salvage it to disk first, then utilize this reveal to decrypt the file:
gpg –output decrypted_message.txt –decrypt letter.gpg
This is in a position to perchance well net a brand new file “decrypted_message.txt” utilizing the encrypted recordsdata from “letter.gpg.” The computer can read which public key encrypted the suggestions (so I don’t must specify a Key_ID), and it will take a look at it has the inner most key to that public key in the keyring, so it’ll utilize it to decrypt the message.
Conclusion
I’ve proven you the steps to net a private and public key for yourself, encrypt a message with my public key, and send me the message which I will decrypt with my inner most key.
Whenever you send me your public key, or directions to net it, I can encrypt a message and send you a message in the occasion you cherish.