The U.S. Division of Justice (DOJ) announced in a February 2022 observation that it had efficiently seized the majority of the bitcoin drained in a 2016 hack of the cryptocurrency swap Bitifinex after gaining retain watch over of the pockets supposedly containing the stolen funds.
No matter the disagreeable unlikelihood of retaking long-gone funds, a advanced but deterministic path of evidence allowed laws enforcement to care for shut Ilya Lichtenstein and Heather Morgan, a couple that used to be allegedly making an strive to obfuscate the illegal origins of the bitcoin they had been leveraging to flex luminous lifestyles by a advanced money laundering draw.
Nevertheless what appeared to be a fastidiously-idea-out scam in point of fact became out to be a relatively fragile one stuffed with missteps, which facilitated the work of special agent Christopher Janczewski, assigned to the Internal Earnings Service’s felony investigation unit (IRS-CI). This work someway led to Janczewski filing a complaint with make a decision Robin Meriweather to payment Lichtenstein and Morgan for money laundering conspiracy and conspiracy to defraud the United States.
This text takes a deep dive into the nuances of the laws enforcement work that uncovered the identities of the accused Bitfinex hackers, and into the steps of the charged couple, counting on the accounts supplied by the DOJ and special agent Janczewski. Then over again, since important aspects of the investigation haven’t been disclosed by official documents, the author will provide believable scenarios and that which you would per chance well be reflect of explanations to questions that remain unanswered.
How Did Regulation Enforcement Do away with The Stolen Bitfinex Bitcoin?
Bitcoin proponents in general boast relating to the monetary diagram’s self-discipline of principles that lets in a excessive degree of sovereignty and resistance to censorship, making Bitcoin transactions very unlikely to be stopped and bitcoin holdings very unlikely to be seized. Nevertheless, if that’s comely, how then used to be laws enforcement in a position to care for a retain of the launderers’ bitcoin on this case?
In step with the complaint filed by special agent Janczewski, laws enforcement used to be in a position to discover internal Litchestein’s cloud storage where he saved grand if not all of the sensitive knowledge associated to his operations as he attempted to clear the dirty funds — including the private keys of the Bitcoin pockets retaining a really powerful a part of stolen BTC.
The censorship resistance of Bitcoin transactions and the sovereignty of bitcoin funds count on the factual facing of the associated non-public keys, as they are the correct formulation to whisk bitcoin from one pockets to 1 other.
Even though Lichtenstein’s non-public keys were saved in cloud storage, in step with the DOJ they were encrypted with a password so long that even sophisticated attackers would doubtlessly not had been in a position to crack it of their lifetime. The DOJ did not reply to a build a query to for comment on the blueprint in which it used to be in a position to decrypt the file and discover entry to the private keys.
There are about a believable scenarios for the vogue laws enforcement used to be in a position to crack Lichtenstein’s encryption. Even though not unnerved in and of itself, symmetric encryption, which leverages an encryption password for both encrypt and decrypt functions, is most sharp as gain as its password and that password’s storage.
Attributable to this reality, the first risk pertains to the safety of the password’s storage; laws enforcement will hang purchased discover entry to to the password one way or the opposite and didn’t want to brute force its formulation by the recordsdata in the cloud. But every other blueprint for laws enforcement being in a position to decrypt Lichtenstein’s recordsdata could well well hang it having so grand extra deepest knowledge relating to the couple and computing vitality than every other sophisticated attacker on this planet that a tailored attack to decrypt focused recordsdata could well well in point of fact be viable whereas not contradicting the DOJ’s statements. We also don’t know the algorithm outdated in the encryption draw — some are extra sturdy than others and variations in the identical algorithm also pose utterly different security dangers — so the instruct algorithm outdated could well well had been extra at risk of cracking, even supposing this would per chance contradict the DOJ claims relating to crackability above.
The almost definitely case of the three is arguably that laws enforcement didn’t want to decrypt the file in the first self-discipline, which is great, especially given the DOJ feedback above. Particular agent Janczewski and his team will hang received discover entry to to the password one way or the opposite and wouldn’t want to brute force its formulation by the cloud storage’s recordsdata. This shall be facilitated by a Third celebration that Lichtenstein entrusted with the creation or storage of the decryption password, or by some form of misstep by the couple that led to the password being compromised.
Why Sustain Internal most Keys On Cloud Storage?
Reasons why Lichtenstein would retain this form of sensitive file in an on-line database is unclear. Then over again, some speculation pertains to the underlying hack — an act for which the couple has not been charged by laws enforcement — and the need for having the pockets’s non-public keys saved on the cloud “as this permits distant discover entry to to a Third celebration,” in step with a Twitter thread by Ergo from OXT Compare.
The cooperation assumption also supports the case for symmetric encryption. Whereas uneven encryption is effectively designed for sending and receiving sensitive knowledge — as the knowledge is encrypted the usage of the recipient’s public key and can most sharp be decrypted the usage of the recipient’s non-public key — symmetric encryption is supreme for sharing discover entry to to a stationary file as the decryption password will be shared between the two occasions.
But every other reason for retaining the private keys on-line could well well be straightforward lack of care. The hacker could well well simply hang idea their password used to be gain ample and fell for the convenience of getting it on a cloud provider that will be accessed anywhere with an net connection. Nevertheless this scenario aloof doesn’t reply the search info from of how the couple received discover entry to to the private keys associated to the hack.
Protecting the private key on-line for convenience is great, supplied the hackers lacked sufficient technical knowledge to be drag that a accurate ample symmetric encryption setup or simply assumed their association couldn’t be breached.
Bitfinex declined to comment on any small print known relating to the hacker or whether or not they are aloof being tracked down.
“We can’t comment on the specifics of any case beneath investigation,” Bitfinex CTO Paolo Ardoino told Bitcoin Journal, including that there are “inevitably a range of occasions enthusiastic” in “this form of predominant security breach.”
How Did Lichtenstein And Morgan Earn Caught?
The complaint and DOJ’s observation alleges that the couple employed several methods to strive to launder the bitcoin, including chain hopping and the usage of pseudonymous and industry accounts at several cryptocurrency exchanges. So, how did their actions discover observed? It largely boils down to patterns and similarities paired with carelessness. Bitfinex also “worked with world laws enforcement companies and blockchain analytics companies” to learn discover better the stolen bitcoin, Ardoino acknowledged.
Lichtenstein would mechanically birth up accounts on bitcoin exchanges with fictitious identities. In one instruct case, he allegedly opened eight accounts on a single swap (Poloniex, in step with Ergo), which at the birth were apparently unrelated and never trivially linkable. Then over again, all of those accounts shared extra than one characteristics that, in step with the complaint, gave the couple’s identity away.
First, all of the Poloniex accounts outdated the identical email provider basically basically based in India and had “in the same sort styled” email addresses. 2nd, they were accessed by the identical IP take care of — a predominant red flag that makes it trivial to care for shut the accounts were controlled by the identical entity. Third, the accounts were created around the identical time, shut to the Bitfinex hack. Additionally, all accounts were abandoned following the swap’s requests for further deepest knowledge.
The complaint also alleges that Lichtenstein joined extra than one bitcoin withdrawals collectively from utterly different Poloniex accounts into a single Bitcoin pockets cluster, after which he deposited into an legend at a bitcoin swap (Coinbase, in step with Ergo), for which he had beforehand supplied know-your-customer (KYC) knowledge.
“The legend used to be verified with pictures of Lichtenstein’s California driver’s license and a selfie-vogue characterize,” per the complaint. “The legend used to be registered to an email take care of containing Lichtenstein’s first title.”
By assuming that he had already cleansed the bitcoin, and sending it to a KYC’d legend, Lichtenstein undid the pseudonymity the previous accounts had performed with India-basically basically based email accounts, as he hinted to laws enforcement that he owned the funds from those initial withdrawals that were clustered collectively. And the complaint alleges that Lichtenstein also saved a spreadsheet in his cloud storage containing detailed knowledge about all eight Poloniex accounts.
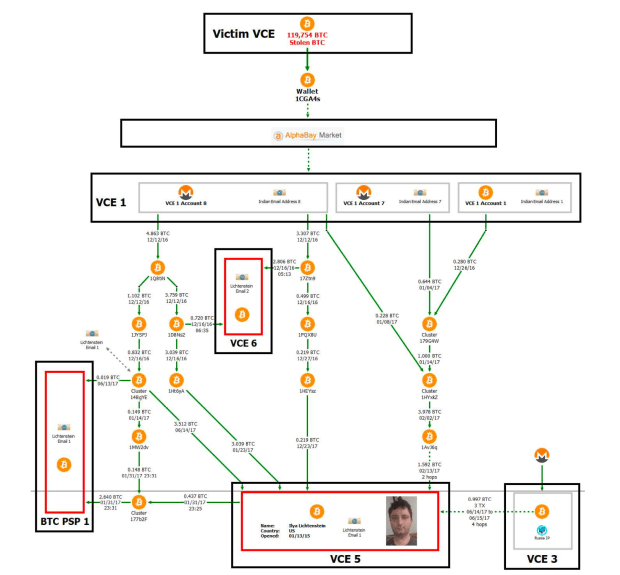
With regards to on-chain knowledge, Ergo told Bitcoin Journal that it will probably be very unlikely for a passive observer to assess the validity of many of the complaint’s claims for the reason that darknet marketplace AlphaBay used to be outdated early on as a passthrough.
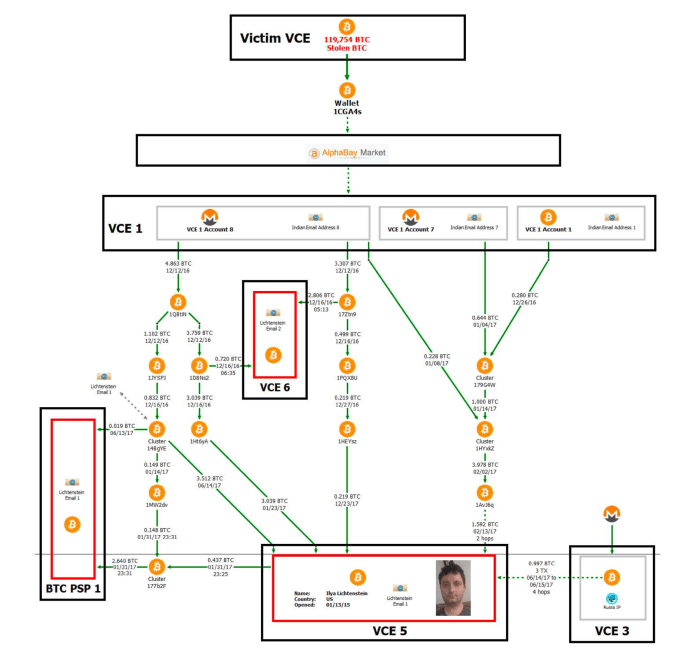
The complaint small print the drift of funds after the Bitfinex hack, but the AlphaBay transaction knowledge isn’t auditable by outsider observers, who attributable to this reality can’t trace the funds themselves. Image provide: DOJ.
“The investigation could well be very straight-ahead, but it absolutely requires insider knowledge of whisk-custodial entity flows,” Ergo told Bitcoin Journal. “As an illustration, the [U.S. government] and chain surveillance companies hang shared the AlphaBay transaction historical past which has no precise on-chain fingerprint and we don’t hang discover entry to to that knowledge. That’s about where I with out a doubt must terminate any diagnosis as a passive observer.”
But every other key a part of info is pockets cluster “36B6mu,” which used to be formed by bitcoin withdrawals from two accounts at Bittrex, in step with Ergo, which had been fully funded by Monero deposits. Wallet cluster 36B6mu used to be then outdated to fund utterly different accounts at other bitcoin exchanges, which, even supposing it did not hang KYC knowledge on the couple, in step with the complaint, 5 utterly different accounts on the identical swap outdated the identical IP take care of, hosted by a cloud provider in New York. As the provider handed its data to laws enforcement, it used to be known that that IP used to be leased by an legend in the title of Lichtenstein and tied to his deepest email take care of.
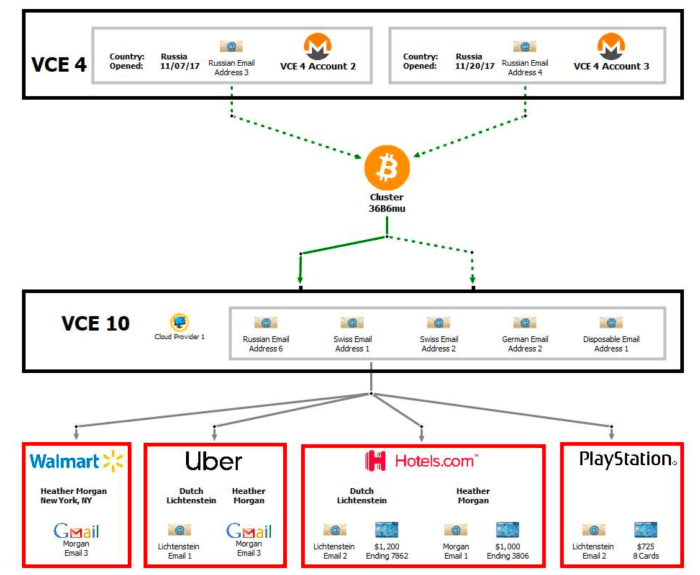
The couple assumed that by funding an swap legend with Monero and withdrawing BTC they would hang “clear” funds, on the opposite hand, a subsequent path of KYC knowledge used to be outdated to deanonymize their fictitious identities across utterly different custodial services. Image provide: DOJ.
Ergo acknowledged the OXT team wasn’t in a position to validate any claims relating to the 36B6mu cluster.
“We sought for the 36B6mu take care of that would correspond to the cluster and chanced on a single take care of,” Ergo acknowledged, sharing a hyperlink to the take care of chanced on. “Nevertheless the take care of will not be portion of a outmoded pockets cluster. Extra, the timing and volumes don’t appear to correspond with those notorious in the complaint.”
“Per chance it’s a typo? So we weren’t in a position to basically validate anything to dwell with the 36B6mu cluster,” Ergo added.
Bitcoin Privateness Requires Draw — And Consideration
Aside from the sections that could well well not be independently attested by external observers, after inspecting the complaint, it becomes clear that Lichtenstein and Morgan deposited utterly different stages of belief of their setup and in different services as they allegedly attempted to use the bitcoin from the hack.
In the starting up, Lichtenstein and Morgan maintained sensitive documents on-line, in a cloud storage provider at risk of seizure and subpoenas. This observe will enhance the possibilities that the setup could well well be compromised, as it makes such recordsdata remotely accessible and deposits belief in a centralized company — which is on no legend a correct idea. For hardened security, important recordsdata and passwords could well well aloof be saved offline in a gain build, and ideally spread out in utterly different jurisdictions.
Belief compromised many of the couple’s efforts in racy the bitcoin funds. The predominant provider they trusted used to be the substantial darknet market AlphaBay. Even though it is miles unclear how laws enforcement used to be in a position to procedure their AlphaBay exercise — even even supposing the darknet market has suffered extra than one security breach since 2016—– the couple on the opposite hand looks to hang assumed this could well well on no legend occur. Nevertheless almost definitely most importantly, darknet markets in general raise suspicion and are always a predominant focal level of laws enforcement work.
Assumptions are perilous attributable to they’re going to lead you to collapse your guard, which in general triggers missteps which a savvy observer or attacker can leverage. On this case, Lichtenstein and Morgan assumed at one level they had employed so many methods to obfuscate the provision of funds that they felt gain in depositing that bitcoin into accounts possessing their in my opinion-identifiable knowledge — an circulation that could well well ensue a cascading, backwards assemble to deanonymize most if not all of the previous transactions.
But every other red flag in the couple’s facing of bitcoin pertains to clustering collectively funds from utterly different sources, which permits chain diagnosis companies and laws enforcement to plausibly care for shut the identical particular person controlled those funds — one other backwards deanonymization replacement. There shall be no memoir of the usage of mixing services by the couple, which will’t erase past exercise, but can provide correct ahead-searching privacy if performed precisely. PayJoin is one other tool that will be leveraged to elevate privacy when spending bitcoin, even supposing there is no such thing as a memoir of the couple the usage of it.
Lichtenstein and Morgan did strive to dwell chain hopping as but every other for obtaining spending privacy, a technique that attempts to ruin on-chain fingerprints and thus, heuristic links. Then over again, they performed it by custodial services — largely bitcoin exchanges — which undermine the observe and introduce an pointless trusted third celebration that will be subpoenaed. Chain hopping is neatly performed by witness-to-witness setups or atomic swaps.
Lichtenstein and Morgan also tried the usage of pseudonymous, or fictitious, identities to birth accounts at bitcoin exchanges to conceal their precise names. Then over again, patterns in doing so led observers to change into extra attentive to such accounts, whereas an IP take care of most regularly removed doubts and enabled laws enforcement to care for shut the identical entity controlled all of those accounts.
Handsome operational security in general requires that every identity be utterly isolated from others by the usage of its hang email provider and take care of, having its hang uncommon title and most importantly, the usage of a separate tool. Repeatedly, a sturdy setup will also require each utterly different identity to use a definite VPN provider and legend that doesn’t retain logs and does not hang any ties to that user’s precise world identity.
Since Bitcoin is a clear monetary community, funds can with out concerns be traced across funds. Internal most use of Bitcoin, attributable to this reality, requires knowledge relating to the functioning of the community and utmost care and effort over time to manufacture obvious the littlest quantity of missteps as that which you would per chance well be reflect of whereas abiding by clear operational guidelines. Bitcoin isn’t anonymous, but it absolutely isn’t incorrect either; use of this sovereign money requires procedure — and a focus.
What Will Happen To The Recovered Bitcoin?
Even though the couple had been charged with two offenses by U.S. laws enforcement, there’ll aloof be a judging task in courtroom to resolve whether or not they are chanced on responsible or not. In the tournament that the couple is chanced on responsible and the funds are sent assist to Bitfinex, the swap has an circulation conception, Ardoino told Bitcoin Journal.
“After the 2016 hack, Bitfinex created BFX tokens, and gave them to affected customers on the rush of 1 coin for every $1 misplaced,” Ardoino acknowledged. “Within eight months of the safety breach, Bitfinex redeemed the total BFX tokens with bucks or by exchanging the digital tokens, convertible into one general fraction of the capital stock of iFinex Inc. Roughly 54.4 million BFX tokens were converted.”
Month-to-month redemptions of BFX tokens started in September 2016, Ardoino acknowledged, with the closing BFX token being redeemed in early April of the following twelve months. The token had begun trading at roughly $0.20 but frequently elevated in value to almost $1.
“Bitfinex also created a tradeable RRT token for certain BFX holders that converted BFX tokens into shares of iFinex,” Ardoino outlined. “After we efficiently discover better the funds we can fabricate a distribution to RRT holders of up to 1 buck per RRT. There are approximately 30 million RRTs outstanding.”
RRT holders hang a priority disclose on any recovered property from the 2016 hack, in step with Ardoino, and the swap could well well redeem RRTs in digital tokens, money or other property.