Dwelling » Ecosystem » North Korea’s Lazarus Team devices up fictitious US corporations to farm dev wallets
Apr. 25, 2025
North Korean hackers exploit correct loopholes to avoid sanctions and purpose digital sources with malware.

Key Takeaways
- Lazarus Team residing up untrue US corporations to accommodate crypto alternate builders with malware.
- The operation represents an evolution in North Korea’s efforts to accommodate the crypto sector for funding.
Allotment this article
North Korea’s Lazarus Team, thru its subunit, spun up untrue US-registered corporations as a part of a campaign to phish crypto builders and grab their wallets, per a brand novel memoir from Reuters.
The corporations, Blocknovas LLC and Softglide LLC, had been registered in Contemporary Mexico and Contemporary York the employ of untrue personas and addresses. One other entity, Angeloper Company, is reportedly linked to the operation, but it undoubtedly is no longer registered in the US.
The blueprint
The tactics fervent growing untrue corporations, setting up a convincing online presence, and posting job listings focusing on builders.
Hackers extinct false identities, made-up addresses, and right platforms devour LinkedIn and Upwork to appear official and entice builders. As soon as candidates opted in, they had been taken thru untrue interviews and instructed to download take a look at assignments or design.
These recordsdata contained malware that, once completed, gave attackers entry to the victim’s system, allowing them to extract passwords, crypto wallet keys, and quite a lot of sensitive files.
Russian-speaking neighborhood extinct almost the same tactics in earlier campaign
In February, BleepingComputer reported that Loopy Rude, a Russian-speaking cybercrime neighborhood, had already deployed associated tactics in a targeted scam in opposition to crypto and web3 job seekers.
A subgroup of Loopy Rude created a untrue company known as ChainSeeker.io, posting spurious listings on platforms devour LinkedIn. Applicants had been directed to download a malicious app, GrassCall, which installed malware designed to grab credentials, crypto wallets, and sensitive recordsdata.
The operation used to be successfully-coordinated, the employ of cloned websites, untrue profiles, and Telegram to distribute malware.
FBI confirms North Korean link
Kasey Handiest, director of menace intelligence at Restful Push, acknowledged right here is one amongst the predominant identified conditions of North Korean hackers constructing legally registered corporations in the US to avoid scrutiny and function credibility.
Restful Push traced the hackers support to the Lazarus Team and confirmed multiple victims of the campaign, figuring out Blocknovas as the most energetic of the three front corporations they uncovered.
The FBI seized Blocknovas’ domain as a part of enforcement actions in opposition to North Korean cyber actors who extinct untrue job postings to distribute malware.
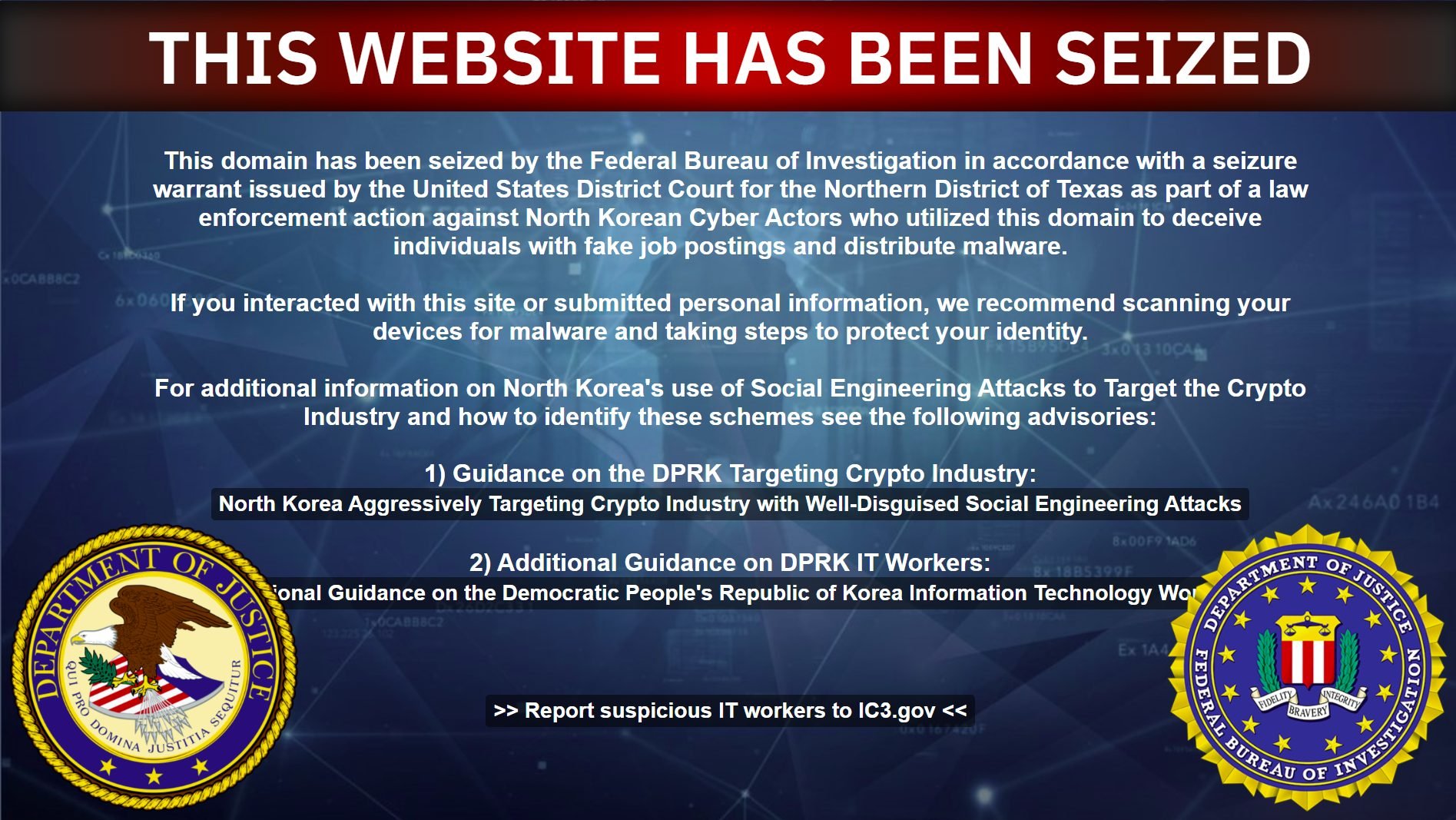
FBI officials acknowledged they proceed to “handle imposing dangers and consequences, no longer simplest on the DPRK actors themselves, but somebody who’s facilitating their ability to conduct these schemes.”
Per an FBI legit, North Korean cyber operations are among the nation’s most sophisticated power threats.
North Korea leverages Russian infrastructure to scale attacks
To overcome small home cyber web entry, North Korea’s hacking neighborhood uses global infrastructure, particularly Russian IP ranges hosted in Khasan and Khabarovsk, towns with order ties to North Korea, per an in-depth diagnosis from Style Micro.
The employ of VPNs, RDP classes, and proxy companies and products devour Astrill VPN and CCProxy, Lazarus operatives are ready to administer attacks, keep up a correspondence via GitHub and Slack, and entry platforms equivalent to Upwork and Telegram.
Researchers at Restful Push fill identified seven instructional videos recorded by accounts linked to BlockNovas as a part of the operation. The videos portray how one can residing up expose-and-alter servers, grab passwords from browsers, add stolen files to Dropbox, and crack crypto wallets with instruments equivalent to Hashtopolis.
From theft to teach-sponsored espionage
Hundreds of builders had been targeted, with many unknowingly exposing their sensitive credentials. Some breaches seem to fill escalated past theft, suggesting Lazarus might well perhaps even fill handed over entry to quite a lot of teach-aligned groups for espionage capabilities.
US, South Korean, and UN officials fill confirmed to Reuters that North Korea’s hackers fill deployed thousands of IT workers out of the country to generate millions in funding for Pyongyang’s nuclear missile program.
Allotment this article


