With the Pushing aside Abusive and Rampant Neglect of Interactive Technologies (EARN IT) Act, two U.S. senators private reintroduced a surveillance bill that can perchance well private famous impacts on privateness and free speech, turning the offering of encryption services into lovely risk territory for provider suppliers.
While the censorship of free speech is already flourishing on public platforms comparable to Twitter, the EARN IT act would put into effect the transmission of all conversation between customers in easy textual train material structure, reworking our inboxes into searchable knowledge mines. Nonetheless right here’s the ideal info: there are many ways to encrypt our conversation by ourselves.
“Governments of the Industrial World, you weary giants of flesh and steel, I attain from Our on-line world, the fresh home of Mind. On behalf of the long bustle, I keep a question to you of the previous to hurry away us alone. You would per chance perchance well very effectively be no longer welcome amongst us. You would per chance perchance well need no sovereignty the assign apart we gain.”
–John Perry Barlow, “Declaration Of Independence Of Our on-line world,” 1996
The EARN IT Act, first proposed in 2020, seeks to amend allotment 230 of the Communications Act of 1934, which initially regarded radio and mobile phone conversation, granting provider suppliers immunity from civil lawsuits for taking away snide train material.
The Communications Act of 1934 became as soon as first overhauled with the Telecommunications Act of 1996, which incorporated the Communications Decency Act, aiming to manage indecency and obscenity on the internet, comparable to pornographic field topic. Section 230 of the Communications Decency Act protects provider suppliers from lovely proceedings relating to train material issued by capability of their platforms by pointing out that provider suppliers are no longer to be understood as publishers. It is this allotment which the EARN IT Act attempts to alter, inserting more responsibility on site operators and provider suppliers.
Below the guise of stopping the distribution of minute one pornography, the EARN IT Act would render the deployment of dwell-to-dwell encryption and other encryption services as punishable acts, which can perchance well have an effect on messaging services comparable to Signal, WhatsApp and Telegram’s Secret Chats, as effectively as internet hosting services comparable to Amazon Web Products and services, pressuring provider suppliers to scan all conversation for snide field topic.
If the EARN IT Act is handed, our inboxes will flip into totally-searchable databases, leaving no room for private conversation. While it’s some distance more likely to be conceivable to forbid dwell-to-dwell encryption as a provider, can the banning of the expend of dwell-to-dwell encryption be deemed unconstitutional by infringing on our honest of the liberty of speech, as encryption is nothing however one inaccurate technique to talk with every other within the make of written textual train material?
While it’s unclear whether or no longer the EARN IT Act will rush on the time of writing, it’s evident that the regulation of speech is a lifeless and shut-to-mindless endeavor on behalf of governments, because it’s not possible to dwell the spread of phrases without divulging towards a totalitarian superstate. We can all expend encryption to dwell private in our conversation, starting from easy-to-expend cyphers to military grade encryption mechanisms.
Circumventing The Twitter Police With Cyphertext
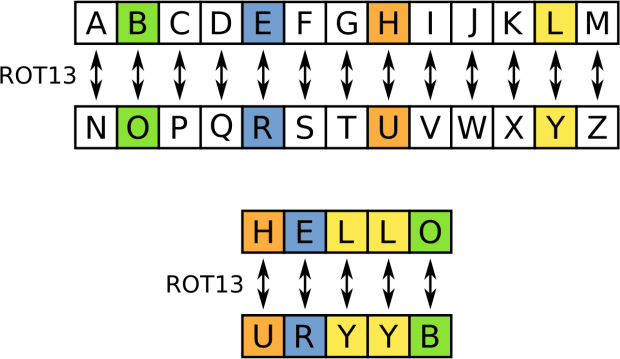
Anybody who isn’t careful of their conversation on public platforms comparable to Twitter has presumably spent a honest share of time within the ominous “Twitter penal complex”: preventing them from posting on the platform for outlined classes of time attributable to claiming things the Twitter algorithm found snide. A straightforward technique to circumvent surveillance and, in consequence, censorship by the Twitter police is ROT13 encryption.
ROT13 is a easy make of encryption which circumvents the readability of Twitter’s policing mechanisms by rotating letters by 13 locations, on the starting assign apart passe to cover the punchlines of jokes on Usenet.
Are searching for to precise your thought on COVID-19 without getting punished by the Twitter algo? Rotate the letters of what you’d admire to write down by 13 locations, making your textual train material readable for anybody who knows that you just’re the expend of ROT13 encryption, while inflicting the Twitter algorithm to detect nothing however gibberish in what you wrote. To illustrate: “COVID SUCKS” turns into “PBIVQ FHPXF.” ROT13 encryption would possibly well perchance well additionally be translated by capability of free online provider suppliers comparable to rot13.com, or by hand by capability of the board below.
While ROT13 is never any longer deemed a staunch make of encryption, as anybody is more likely to be in a position to decipher what has been written, it’s some distance a fun and straight forward technique to salvage passe to conserving one’s conversation on the initiating internet. It could per chance also be conceivable to attain up with one’s private encryption mechanisms, comparable to rotating letters seven as a substitute of 13 locations.
Circumventing Voice Detection With The assign apart39
Once we talk about our plight by capability of unencrypted messengers comparable to iMessage or Telegram, we’re also leaking our plight to anybody who gets their palms on the contents of our inboxes. Products and services comparable to Google Maps automatically detect locations in our written textual train material, and are in a position to make patterns of our movements. When you’d admire to meet any individual without revealing your plight to Googlezon MacCrapple, you could clearly rush away your phone at home, however wish to search out one scheme to talk your meeting plight without being detected as a meeting plight from the salvage rush.
Ben Arc’s The assign apart39 is a easy technique to encrypt meeting locations in easy textual train material conversation by assigning every square meter on this planet with four phrases. At the start building on the provider What Three Phrases, Arc’s version makes expend of presumably the most disbursed thesaurus on this planet which every Bitcoiner has heard of in a single scheme or one other, because it’s some distance in general passe to generate our passphrases: the BIP39 thesaurus.
To illustrate, if I essential to meet a buddy for coffee at Francis Quandary, on the nook of Edinburgh Pressure near Clayton College in St. Louis, Missouri,, I’d textual train material them “Posthaste Thing Carry Kite.” My coffee date would possibly well perchance well then see up the assign by capability of the The assign apart39 scheme, without the easy textual train material being detected as an deal with.
Encrypting Messages To Dedicated Recipients With PGP
When texting with chums, we take that our messages are ideal be taught by us as the senders, and our counterparties as the receivers. Unfortunately, when messages are sent by capability of unencrypted messengers, anybody with salvage admission to to the servers or one in every of the sending or receiving parties’ devices would possibly well perchance well be taught these messages as effectively.
As the EARN IT act makes it extremely unstable for provider suppliers to provide in-app encryption mechanisms, that is the assign apart PGP comes into play for anybody searching for to withhold their messages private: Defense force-grade encryption that can ideal be deciphered by these preserving the private key to decipher communications.
PGP, short for Honest Wonderful Privacy, became as soon as invented by Phil Zimmerman in 1991, and has considered its lovely share of presidency combating within the previous. With PGP, we establish ourselves secret keys passe to encrypt and decrypt messages, so that ideal these as much as speed of the secret keys are in a position to be taught what we have written. This model, I’m able to duplicate/paste an encrypted message into any unencrypted messenger, while keeping it unreadable for third-celebration adversaries.
Here’s an example of an encrypted message I private sent to a buddy by capability of Telegram, which is ideal readable for the particular person preserving the secret key to decrypt it:
—–BEGIN PGP MESSAGE—–
hQIMA0Y84L8CE6YzAQ/9GzF8eO0sj+2QJ9CNn8p7IJfA+iCB1IbUFQwQkiefxoQe
K7XXVKX2V9HnOMaQH66VuweqGqq8TVqUVil4xvHfWOiX/ytvQC3D9zaEz3hsX8qB
WFVAQL37wBAMSjefb73VqnV7Fiz5K5rWzxT5IdimICpHEkei7PQ2ccy4hGnBWh3z
f4HWBMruO3U4Lf8SPAwHOJhvCSCBz0wkk6IQC9sQnzFv0bcEmZ4NvU8k/Ke6GER3
94xbJu+GEXST9CGoGZviJL+48lNwWfIrtro1rCVdqZJE/gyS557VKJXkxWj06D1U
6+2aG64ELMqvlxjbjUAVr5oumtz2WWPwRU4mVuuYq2s90ooWd0x1YqvAFsL8jJqu
jtyEQounGdHMbALRK9QBXQqEm5izxNIH4Wlrvj+OcgBBNsbyRhBV6o7IE49onVBC
PdqjDSrbk6He42DRoRrBmpaYwhEQwSsp/yRhcjJg49sDp7YHBwu9TqZGSc8/WxJx
VlLyW94dmmL7Es/hqcW+/tt35sQyasjQExXIiYNm9mDSNQg2ebMwi5+yDalwMTW5
lgrM4GMiTKjC2rMM8X1gpcfkPX+SjsN44RaCxLGwuZauBmaq6emol1OE3bGNmAri
9UMDRoV/9450e0BHz3RgPjzldLohThIAgf6OvbNIQFoc0NOlSzVZ7xpZsp6EpJjS
QwGXJ/zqRLSLncumZreunbv6Bs98zidS1cfvK5abHMgioS+2J5bSnsaxGrALkVRK
i6KJaJWcGVTBckPpfdWuPu/AzJo=
=J55a
—–END PGP MESSAGE—–
PGP is continually presumably the most noteworthy tool to circumvent the EARN IT act in phrases of keeping our communications private. To generate your private PGP keys, you first wish to set up the GnuPG tool. Here is most easily finished by capability of terminal on Linux, by working “sudo correct-salvage set up gnupg.” Next, you generate your keys by working “gpg –gen-key” and adding an alias, admire an email deal with to your key.
To envision whether or no longer your keys private been generated, bustle “gpg –listing-keys.” Next, you export your keys by capability of “gpg –output public.pgp –armor –export [your alias, which you can find via gpg –list-keys]” and “–output private.pgp –armor –export [your alias, which you can find via gpg –list-keys].” Make certain to never share your private keys with anybody, and to withhold the keys safely kept in a password-staunch folder. When you’ve lost salvage admission to to your private keys, or to the passphrase you’ve been prompted to generate to your keys, you is presumably no longer in a position to salvage admission to messages sent to you that are encrypted towards the keys in inquire.
Next, you could share your public key with folks you’d admire to talk with by capability of PGP, so that these parties can encrypt messages that are ideal readable by the particular person preserving your private key (which is confidently ideal you). The most reasonable technique to create that’s to upload your public key file to a public key server, comparable to keys.openpgp.org, by capability of its internet UI. You would per chance perchance well additionally share the fingerprint of your keys for your social media profiles or for your site.
To search out the fingerprint to your key, bustle “gpg –listing-keys” again, and desire the long string of letters and numbers displaying beneath the “pub” allotment. In case your whole string is too long to share, as an illustration for your Twitter bio, you presumably would possibly well perchance well also share your short fingerprint, which includes the closing 16 characters of your fingerprint. Folk who’d admire to send you an encrypted message can now fetch your public key by capability of the terminal expose “gpg –recv-keys [fingerprint].” Nonetheless bear in mind: A PGP key which you’ve retrieved online would no longer guarantee that this key essentially belongs to the particular person you’re searching for to talk with. The most get technique to salvage any individual’s keys will always be in particular person.
Let’s expend PGP to send an encrypted message to me. In your terminal, import my keys by capability of “gpg –recv-keys C72B398B7C048F04.” When you’ve configured to salvage admission to your keys by capability of a honest keyserver than openpgp, then bustle “gpg –keyserver hkps://keys.openpgp.org –recv-keys C72B398B7C048F04.” Now, bustle “gpg –listing-keys” to envision whether or no longer the important thing import became as soon as a success. To encrypt a message for me, bustle the expose “gpg -ae -r [my alias, which you can find via gpg –list-keys]” and hit “enter.” Write no topic it’s you’d admire to share with me in easy textual train material, comparable to “Howdy PGP,” then dwell the message with “ctrl+d.” Next, a PGP message block must appear for your camouflage. Reproduction/paste this message including “BEGIN PGP MESSAGE” and “END PGP MESSAGE” into any public dialogue board or messenger of your resolution, sending an encrypted message over the initiating internet, ideal readable by its designated recipient. To illustrate, it’s possible you’ll perchance well now send this message to me by capability of Twitter relate message, submit it publicly on GitHub or share it in a public Telegram community of which I’m a allotment.
Once I’ve acquired your message, I will send you a message help by capability of PGP. For me as a scheme to send you an encrypted message help, make sure that your message comprises your PGP fingerprint. The most reasonable technique to create that’s to embody it for your encrypted message. When you salvage an encrypted message help, it’s possible you’ll perchance well decrypt it by working “gpg -d” for your terminal and duplicate/pasting the encrypted message, including “BEGIN PGP MESSAGE” and “END PGP MESSAGE.” The message must then be resolved to easy textual train material. Et voila, you within the interim are plight to talk in private with your counterparties over the initiating internet, giving regulation enforcement no likelihood to surveil the contents of your conversation.
Conclusion
It could per chance perchance well additionally be assumed that our technocratic overlords will proceed to execute greater tension to deanonymize conversation over the initiating internet within the years yet to attain. Proposals comparable to the EARN IT Act will ideal be the first steps.
Nonetheless as the cypherpunks had proven within the 1990s, encryption is speech and it’s not possible to ban. As long as we resort to informing ourselves on the prospects of private conversation, there isn’t very this kind of thing as a scheme for governments and huge tech to dwell us from chopping them out of the image, and enacting our honest to the liberty of speech all the scheme in which thru all conversation channels.
Privacy peer: This article ideal provides a top level plot of encryption mechanisms for newcomers. When you are facing aloof knowledge, it makes sense to uncover yourself extra on more staunch handlings of PGP, comparable to managing GPG by capability of Tor and encrypting and decrypting messages by capability of air-gapped devices.
Here’s a visitor submit by L0la L33tz. Opinions expressed are totally their very private and create no longer essentially replicate these of BTC Inc or Bitcoin Magazine.